FIREMON SOLUTIONS
Zero Trust Network Access
Bridge the gap between your current perimeter-based security infrastructure and zero trust network access (ZTNA) with automated policy management from FireMon.

Bridge the gap between your current perimeter-based security infrastructure and zero trust network access (ZTNA) with automated policy management from FireMon.
Zero trust offers many long-term advantages to organizations looking to secure their assets, protect their users and customers, and harden their defenses to prevent unauthorized access. However, the complexity of adopting a ZTNA solution leaves most organizations wondering where to start - and how far to go.
For most, strategically adopting key zero trust workflows to protect their corporate network will enhance security posture with minimal disruption to operations.
Zero trust isn’t simply a framework or a set of technologies — it’s a mindset. There’s no switch that flips to turn on zero trust. Organizations have to carefully migrate systems to a zero trust architecture while maintaining the operability of existing infrastructure.
FireMon provides the essential pathway for organizations transitioning from a perimeter-based network infrastructure to a zero trust architecture.
FireMon Cyber Asset Management gives your organization a comprehensive view of your network, including everything from physical, cloud-based, virtual, and software-defined network infrastructure and endpoints to operational technology, application access, and the Internet of Things (OT/IoT).
These insights into network traffic data and the current state of enterprise assets are important characteristics in any ZTNA solution by NIST standards.
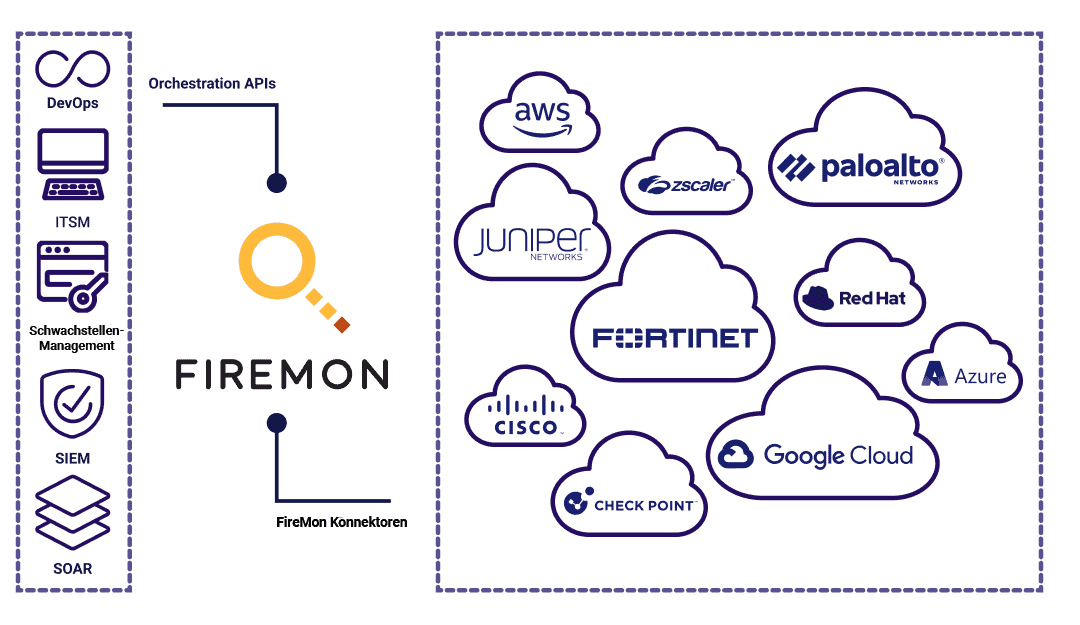
FireMon Policy Manager provides a unified view that normalizes policy content across environments containing multiple firewall vendors, cloud security groups, SD-WAN and SASE offerings.
This capability allows the tenets of zero trust to be actualized in the organization among policy engine, policy administrator, and policy enforcement point components.
This workflow is often facilitated via API integration into an IT Service Management (ITSM) process such as ServiceNow. As the number of security controls increases within a micro-segmented network, FireMon Policy Manager pushes security policy into all policy enforcement points.
The capability to automate ZTNA policy, from design to decommissioning, frees up security teams for more intensive, mission-critical tasks.
Transitioning from a traditional perimeter-based security architecture to zero trust often leaves organizations uncertain about where to begin.
FireMon is one of the best ZTNA solutions, delivering the necessary scalability, flexibility, and real time visibility to support zero trust — driven by robust APIs and airtight integrations.
ZTNA (Zero Trust Network Access) is a security solution that enforces strict identity verification for every user or device attempting to access resources on a network, regardless of their location. Unlike traditional VPNs, ZTNA solutions grant access only to specific applications, reducing the attack surface and enhancing security in dynamic, hybrid environments.
Zero Trust Network Access (ZTNA) works by enforcing strict access control measures, requiring authentication and authorization before users or devices can connect to specific resources. Instead of granting broad access, ZTNA solutions grant access only to authorized applications or data based on identity, device, and security posture, ensuring that each request is verified before access is allowed.
ZTNA (Zero Trust Network Access) and virtual private network (VPN) differ in their approach to security. While a virtual private network grants broad access to the entire network once connected, ZTNA only allows access to specific applications or resources based on user identity and security posture. ZTNA offers more granular control, reducing the attack surface compared to VPNs.