Firewall Rules Change. Maintaining Compliance Can’t.
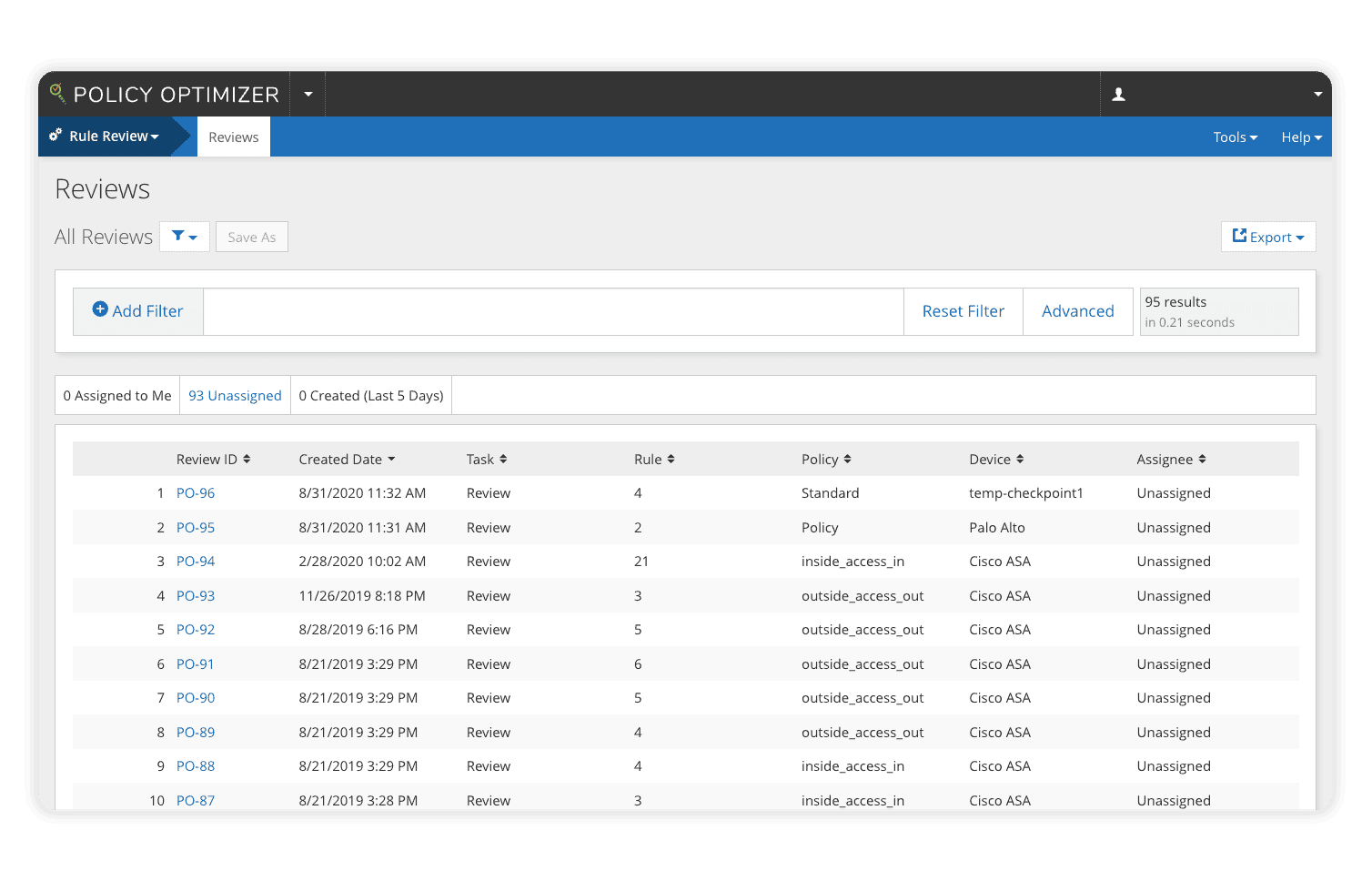
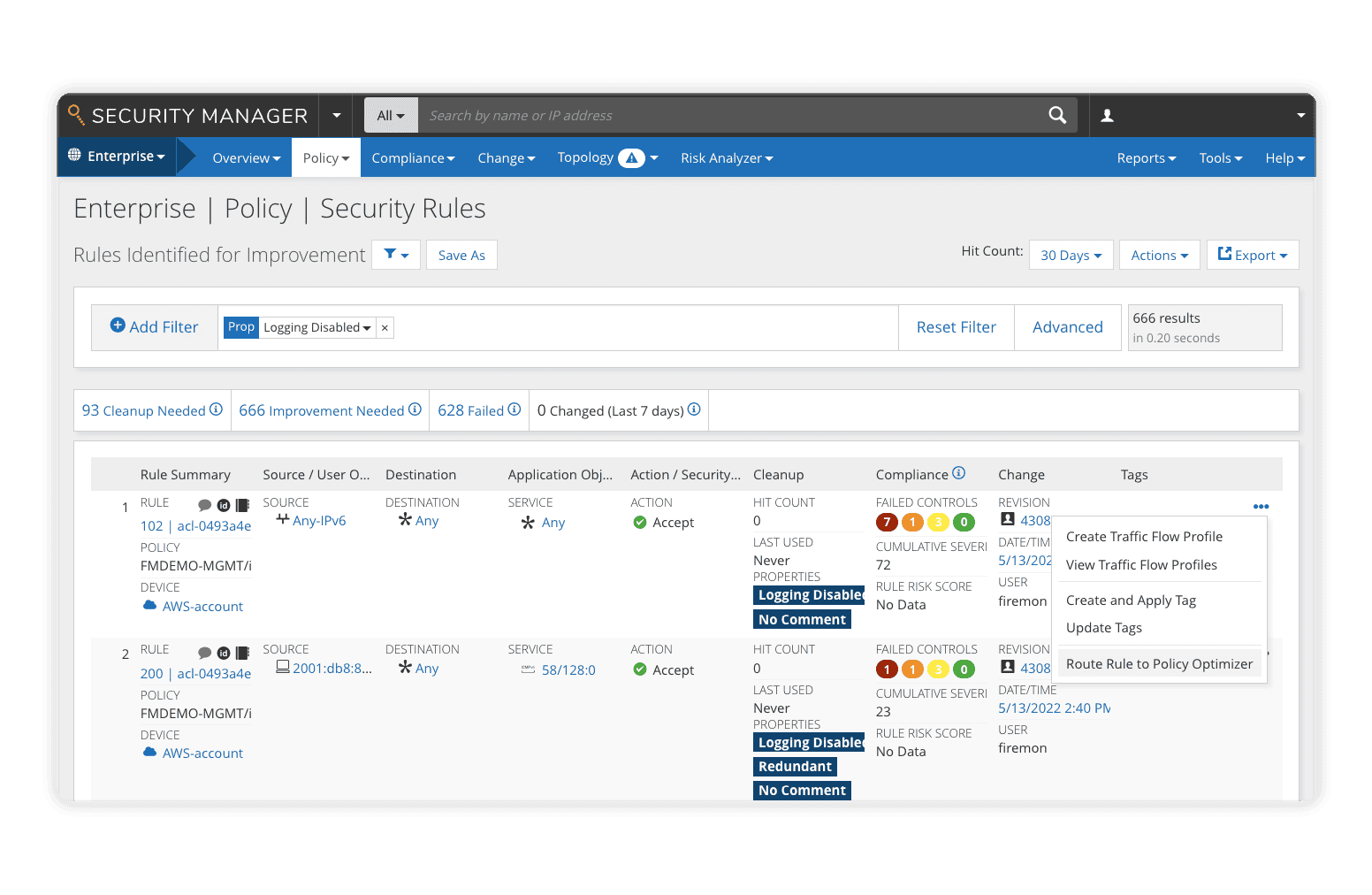
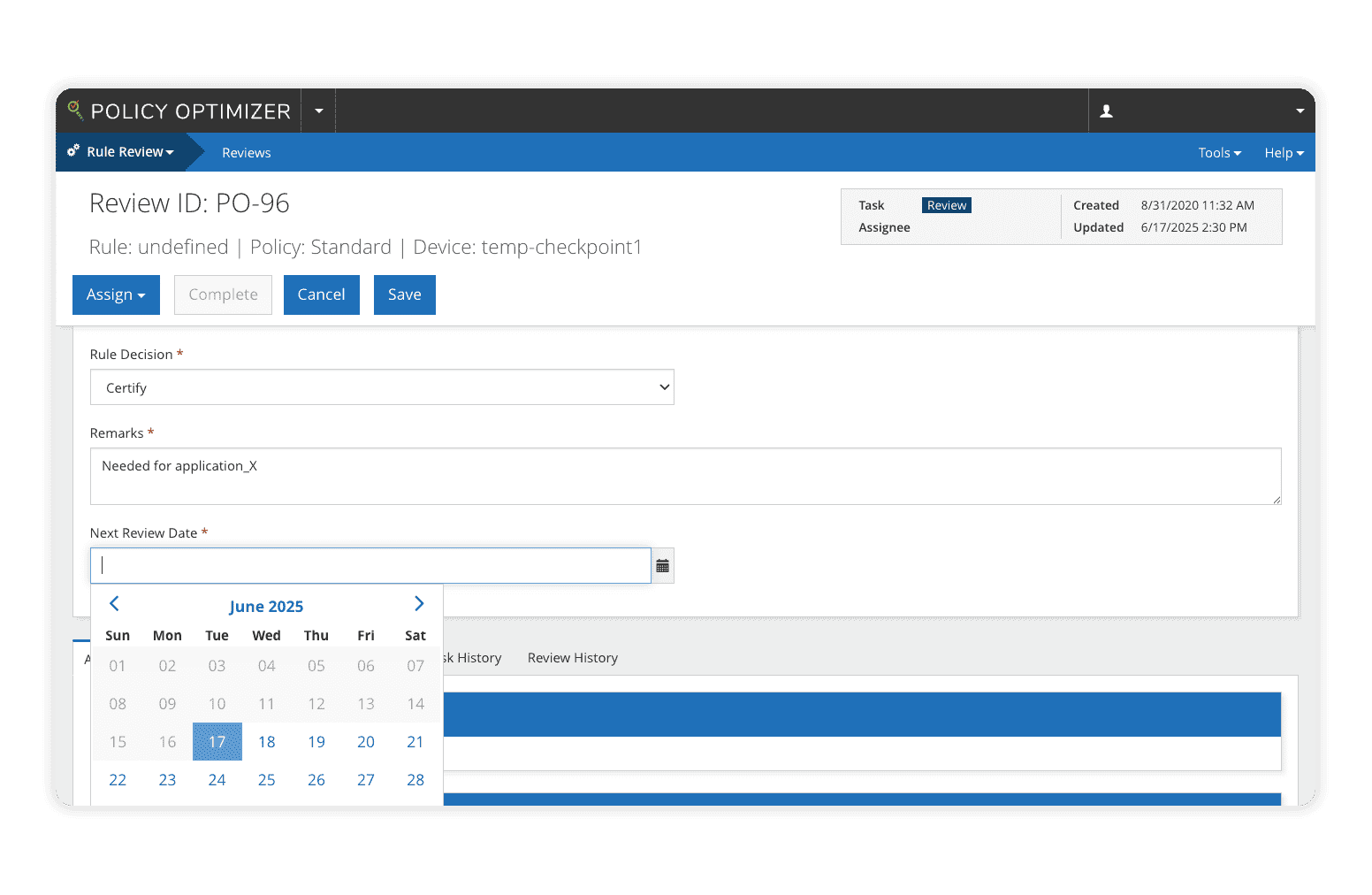
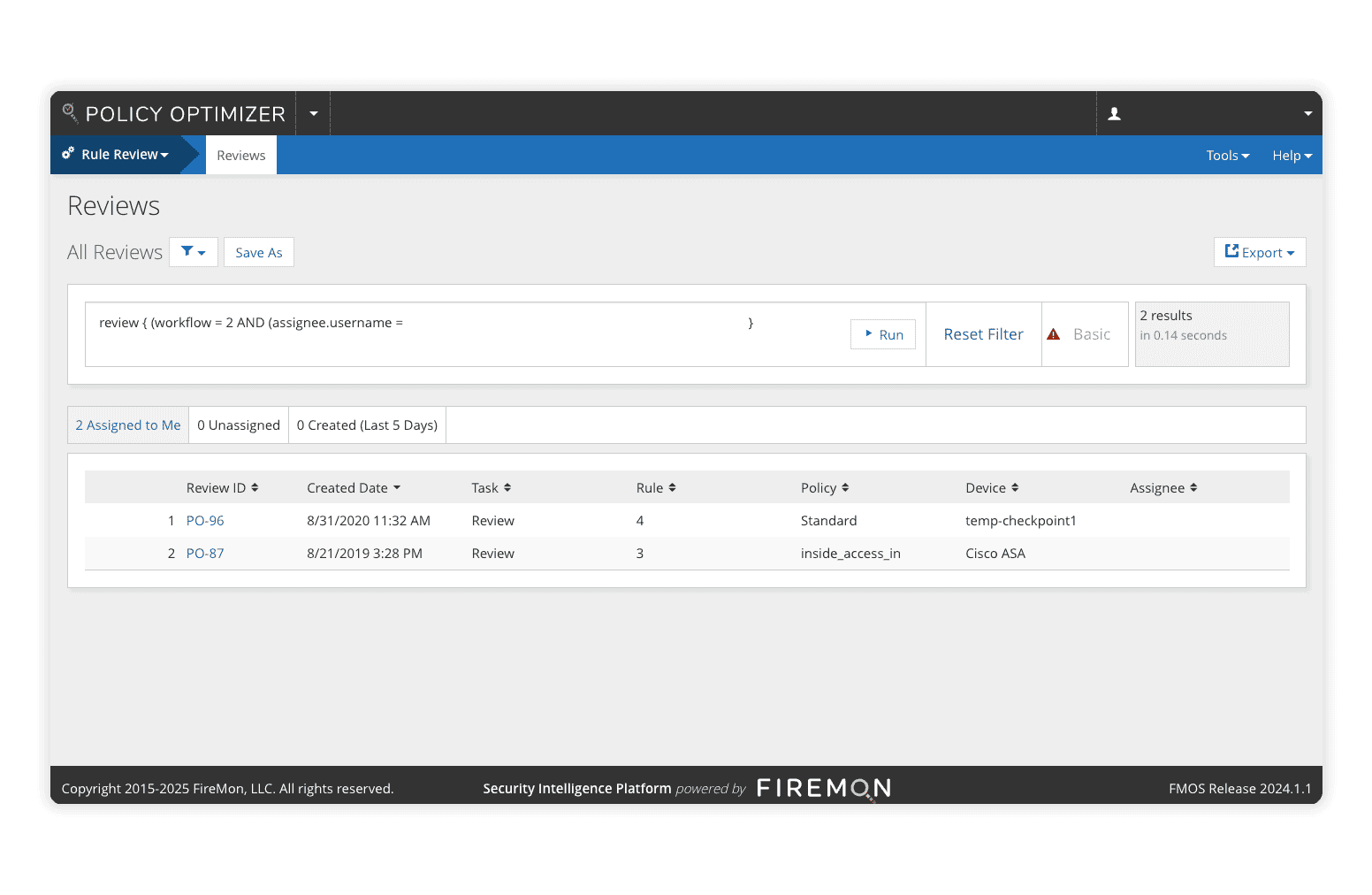
Maintaining and removing policies rarely receives as much attention as their creation. Old policies clutter the network with expired, unused, and overly permissive rules expanding the threat surface, making meeting compliance standards nearly impossible.