Efficiently Manage Network Security and Compliance
Manufacturing organizations are prime targets for cyber-attacks. Complex production environments, with high-value assets spread across multiple facilities, create opportunities for network policy vulnerabilities that can be difficult to detect and address using manual processes. In an industry where even minor downtime or compliance violations can lead to substantial financial losses and disrupt supply chains, FireMon empowers manufacturers to maintain compliance, mitigate the risk of cyber-attacks, and ensure uninterrupted operations.
Why Choose FireMon?
Proactive Threat Response
FireMon helps you quickly identify and respond to threats, ensuring robust network security.
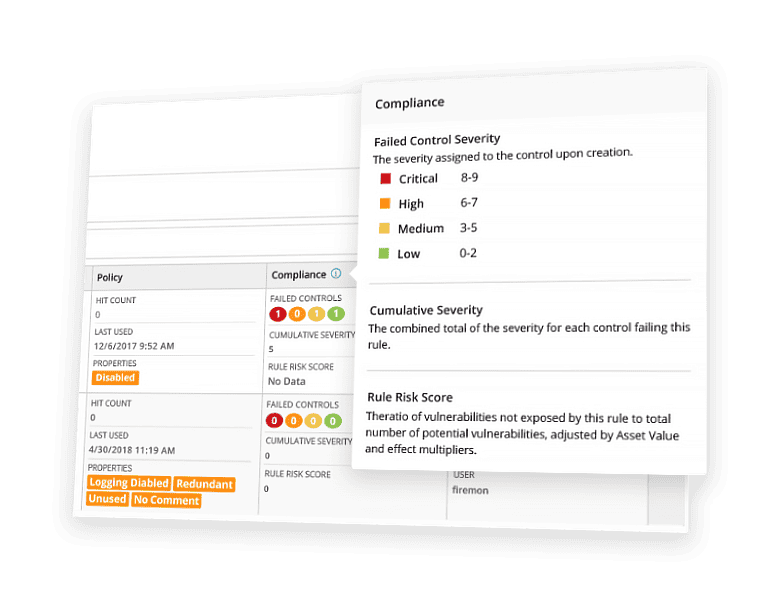
Efficient Compliance Management
Manage compliance with real-time violation detection and advanced risk modeling.
Scalable Solutions
FireMon’s customizable solutions grow with your organization, protecting your valuable data.
Streamlined Manufacturing Compliance
Stay ahead of ever-changing manufacturing regulations with FireMon’s comprehensive compliance solution that simplifies and automates reporting, violation detection, and rule recertification at enterprise scale.
- Manufacturing Specific Compliance Reporting: FireMon provides built-in assessments including NIST, ISO 27001, NERC CIP, and GDPR, while supporting custom assessments using internal business policies, external frameworks, or industry best practices.
- Real-time Violation Detection: Continuous network monitoring over your entire environment with automated alerts that detect violations as they happen, help prevent interruptions that could affect sales and customer confidence.
- Customizable Growth: With performance verified to support 15 thousand devices and 25 million rules coupled with an API-first approach for easy integrations into SIEM, SOAR, vulnerability scanners, and ITSM solutions, FireMon has your current and future security environments covered.
With FireMon’s network security and compliance management services, your organization stands to benefit from enhanced protection, improved efficiencies, and long-term savings.
Frequently Asked Questions about Cybersecurity for Manufacturing
What are some use cases for FireMon’s manufacturing cybersecurity software?
FireMon’s manufacturing cybersecurity software provides continuous monitoring of network security, automated policy management, and real-time threat detection. It secures operational technology (OT) systems, streamlines compliance with industry regulations, and reduces manual effort through automation. Additionally, it enhances incident response with detailed insights and analytics, enabling rapid vulnerability resolution and effective risk mitigation across manufacturing environments.
What are the benefits of using software to manage cybersecurity for manufacturing?
Using software to manage cybersecurity in manufacturing offers real-time monitoring of critical operational technology (OT) systems and automated threat detection. It streamlines compliance with industry regulations and reduces manual errors through automation. This enhances network visibility, safeguards production processes, and mitigates risks, leading to improved operational efficiency and stronger security posture in manufacturing network environments.
Why are manufacturing organizations a main target for network attacks?
Manufacturing organizations are prime targets for network attacks because they rely heavily on interconnected operational technology (OT) systems and often use legacy infrastructure with vulnerabilities. Disruptions can halt production lines, leading to significant financial losses and supply chain issues. Additionally, they possess valuable intellectual property, making them attractive to cybercriminals seeking competitive advantage or financial gain.