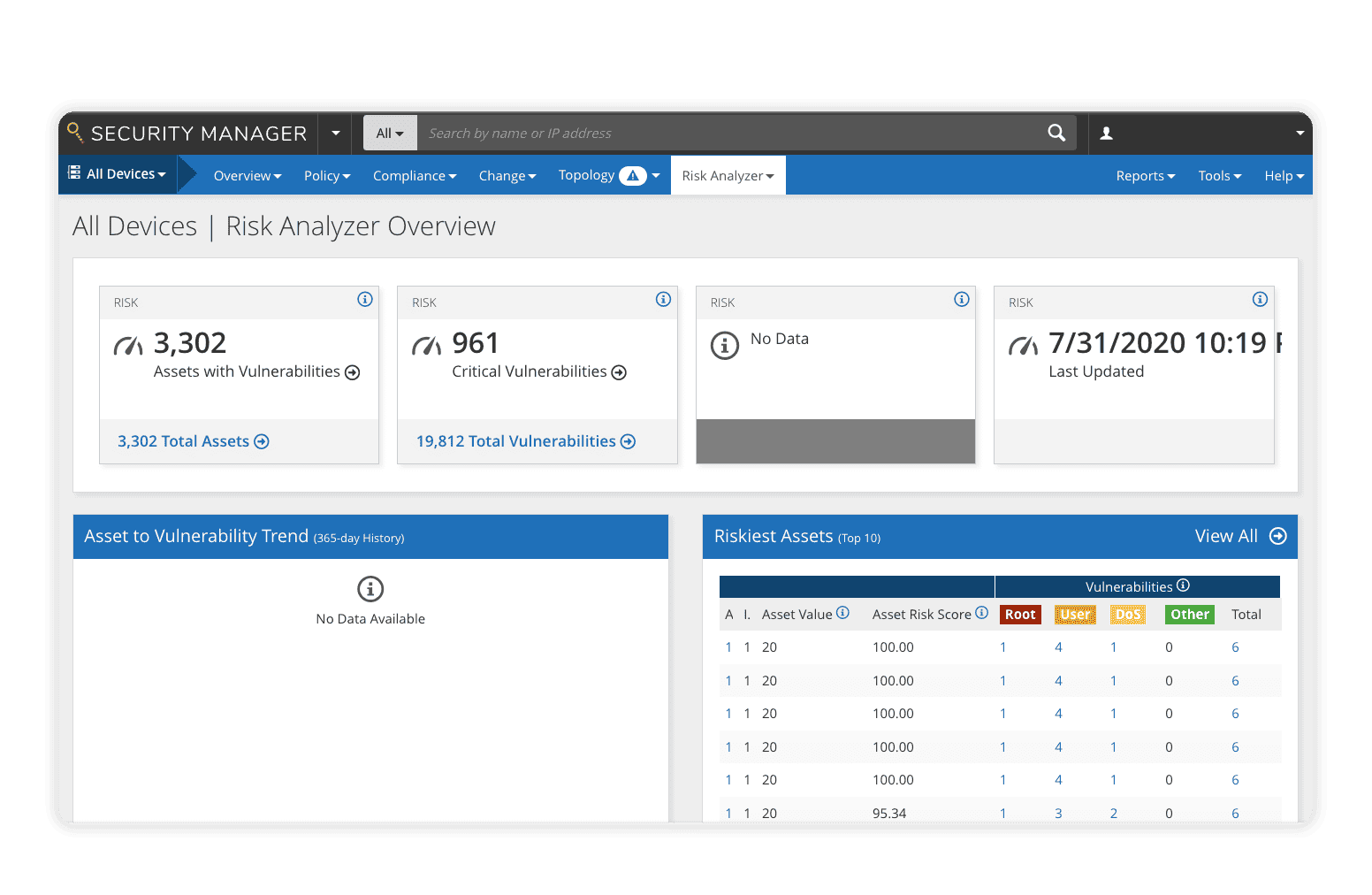
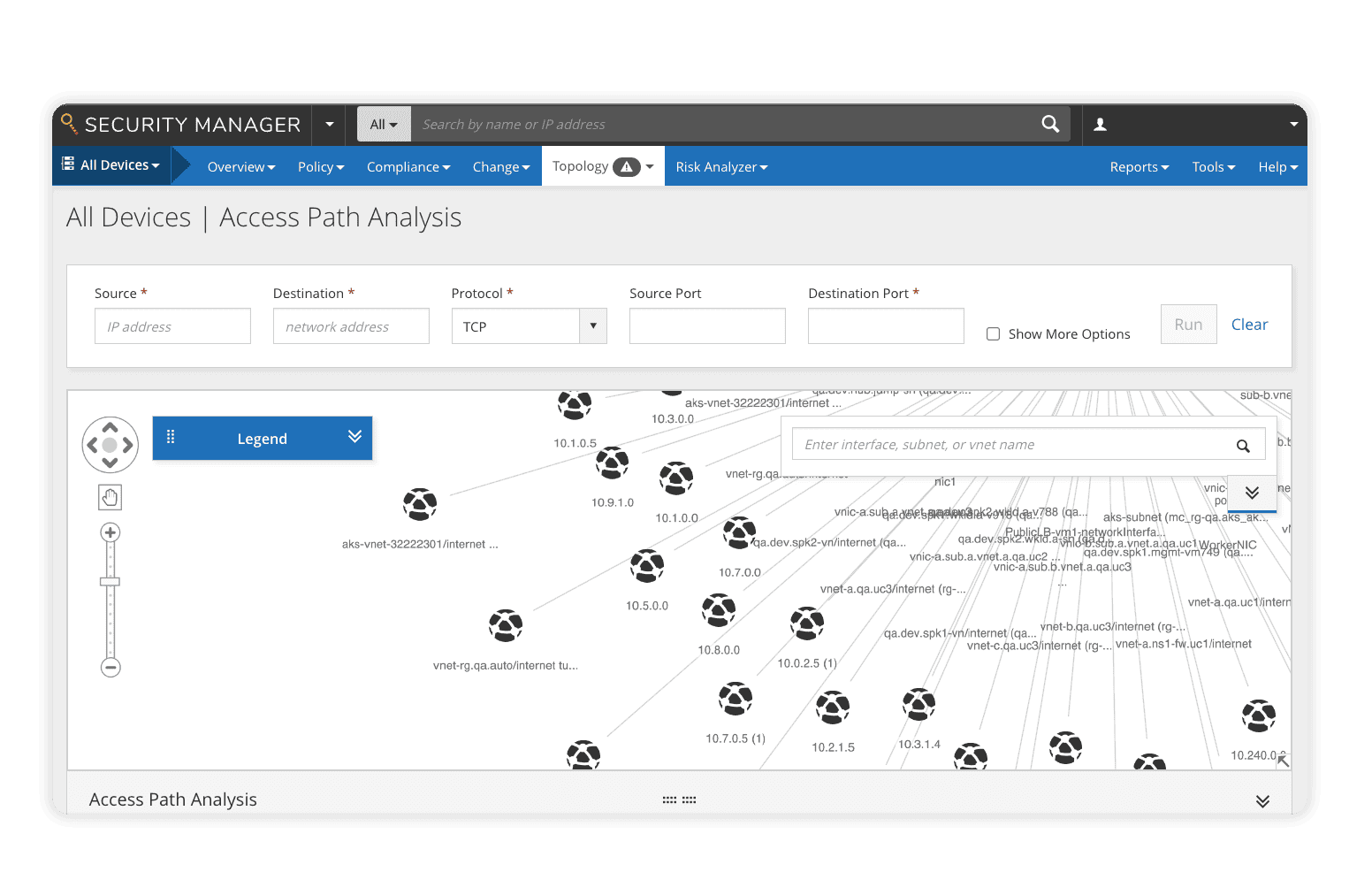
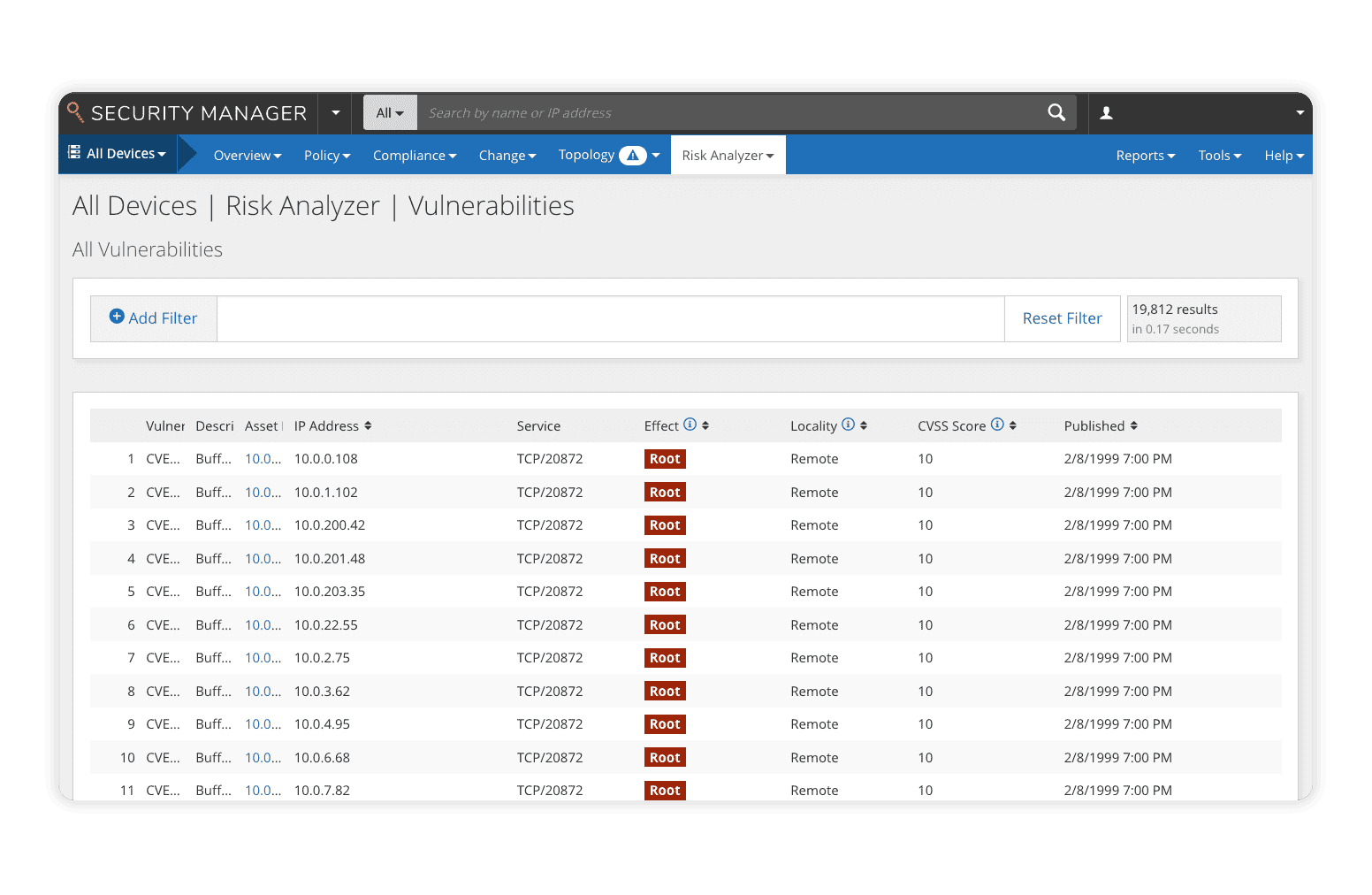
The Risk Analyzer module for Policy Manager provides best-in-class vulnerability management by correlating third-party vulnerability data with network policy, evaluating network risk, and uncovering potential attack paths. Using real-time visibility into network risk posture, Risk Analyzer simulates potential attacks, calculates attack vectors, predicts potential damage, then displays the results in an easy-to-understand user dashboard. Extensive scenario testing helps prioritize vulnerability patching by allowing security teams to simulate patch deployments to determine the impacts to the overall network risk posture.
Risk Analyzer Delivers:
- Consolidated policy risk assessment and reporting with custom and best practices reports
- Risk and threat modeling including attack simulations, change risk simulations, and leak-path detection
- Pre-flight risk checks by automatically scanning for risk prior to change deployment
- Real-time risk detection and response through violation detection, alerts, and mitigation strategy