A LAYERED DEFENSE
Ransomware
FireMon enhances your ability to identify and defend against ransomware attacks
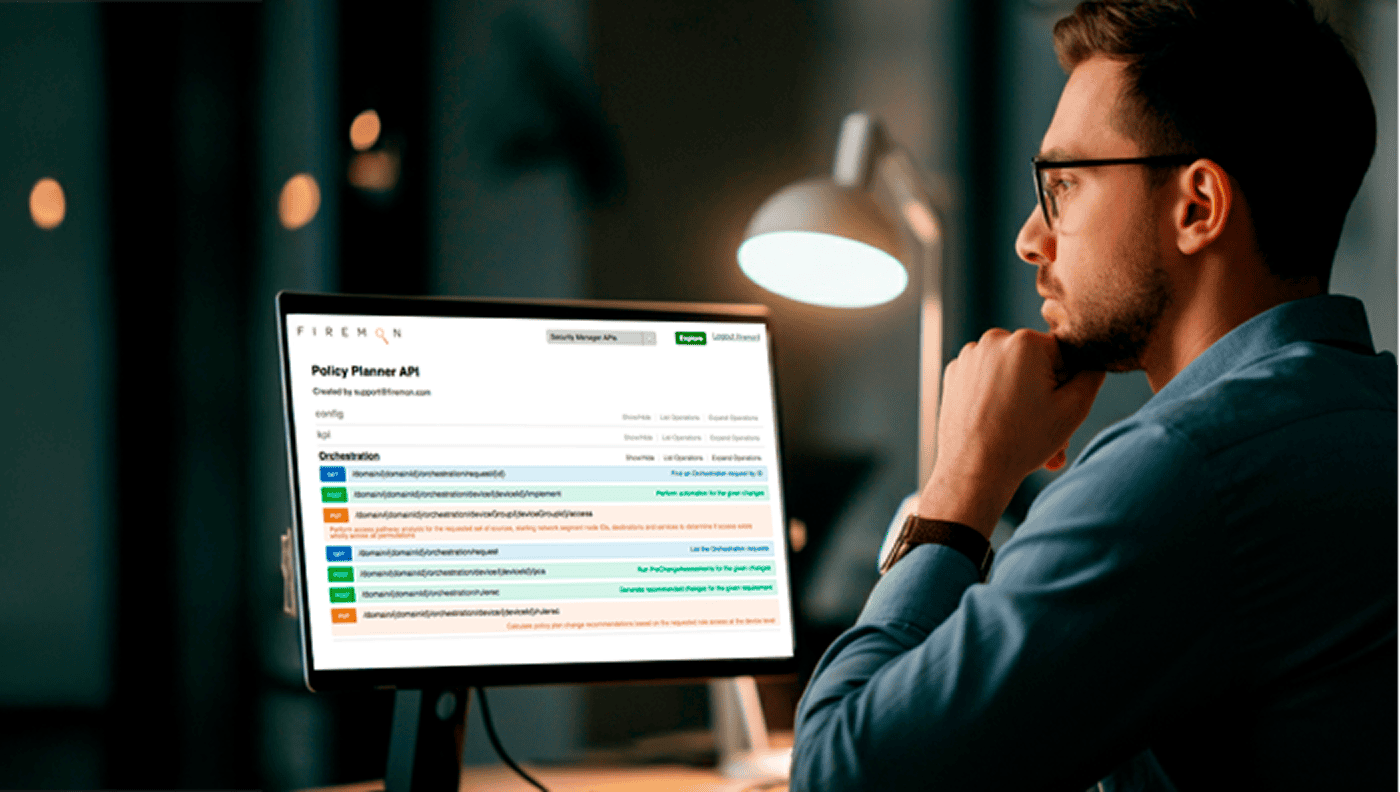
FireMon enhances your ability to identify and defend against ransomware attacks
Ransomware is the top form of malware used by attackers to line their pockets and cause disruption. Many organizations primarily focus on tools that help prevent ransomware, however it’s just as important to have the means to stop its spread should it slip past those defenses.
Every attack leaves behind breadcrumbs and ransomware is no different. Telltale signs usually point to command-and-control in some part of the encryption and exfiltration process. FireMon’s SiCL search can be used to find known ransomware sources and identify policy vulnerabilities that can facilitate spread across the network.
If ransomware penetrates your defenses, network segmentation can help limit its lateral spread across the environment. FireMon’s security policy management tools can be used to create network partitions based on business needs with access granted only to trusted users and/or devices.
A first-rate ransomware defense strategy ensures every element of your network is running the latest software, is updated regularly, and is configured correctly. The first step in this process is to have a complete picture of every device including infrastructure, clouds, and endpoints.
Misconfigured cloud accounts, in particular overly-permissive identities, are vectors that can be exploited by ransomware if compromised. FireMon’s DisruptOps platform monitors your environment against industry best practices to detect critical risks that could lead to or spread a ransomware attack.