Efficiently Manage Telecommunication Network Security
Telecommunications organizations face growing security challenges due to vast, dynamic networks supporting critical infrastructure. With increased traffic, 5G deployment, and cloud integration, manually managing security policies becomes complex and error-prone, leading to vulnerabilities.
In an industry where downtime, breaches, or regulatory non-compliance can result in significant service disruptions and financial loss, FireMon’s telecom network security solutions help maintain continuous compliance, reduce risk and ensure network performance, safeguarding their operations and customers.
Why Choose FireMon for Telecom Cybersecurity?
Proactive Security Threat Response
FireMon helps you quickly identify and respond to cyber threats, ensuring robust network security.
Efficient Compliance Management
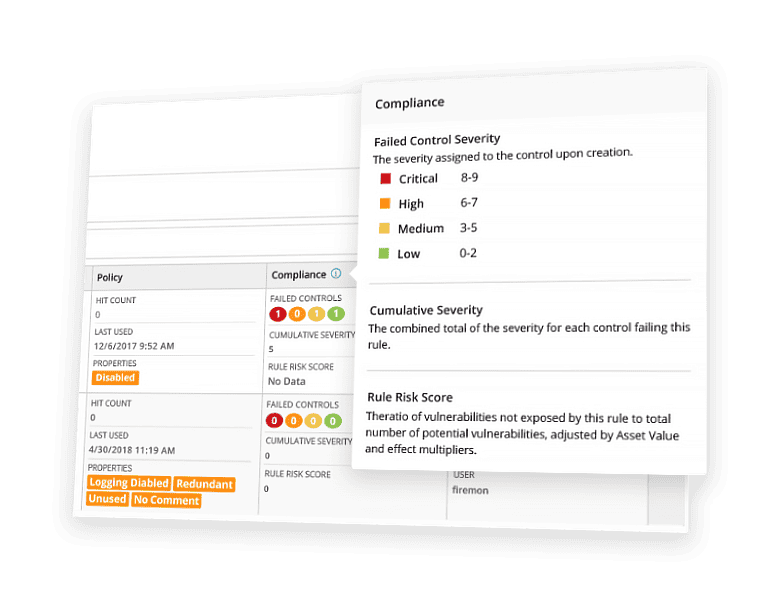
Manage compliance with real-time violation detection and advanced risk modeling.
Scalable Solutions
FireMon’s customizable solutions grow with your organization, protecting your valuable data.
Streamlined Telecommunications Compliance
Stay ahead of ever-changing telecommunications regulations with FireMon’s comprehensive telecom network security that simplifies compliance with automated reporting, violation detection, and rule recertification at enterprise scale.
- Manufacturing-Specific Compliance Reporting: FireMon provides built-in assessments including GDPR, PCI DSS, NIST, and ISO 27001 while supporting custom assessments using internal business policies, external frameworks, or industry best practices.
- Real-time Violation Detection: Continuous network monitoring over your entire environment with automated alerts that detect violations as they happen helps prevent interruptions that could affect sales and customer confidence.
- Customizable Growth: With performance verified to support 15 thousand devices and 25 million rules coupled with an API-first approach for easy integrations into SIEM, SOAR, vulnerability scanners, and ITSM solutions, FireMon has your current and future security environments covered.
With FireMon’s network security and compliance management services, your organization stands to benefit from enhanced protection, improved efficiencies, and long-term savings.
Frequently Asked Questions about Cybersecurity for Telecommunications
What Are Some Use Cases for FireMon’s Telecommunications Software?
FireMon’s telecom cybersecurity software provides continuous monitoring of network security, automated policy management, and real-time threat detection. It secures telecom infrastructure, streamlines compliance with industry regulations, and reduces manual effort through automation. Additionally, FireMon aids in risk assessment, allowing for proactive threat management across complex, large-scale telecom networks.
What Are the Benefits of Using Software to Manage Cybersecurity for Telecoms?
Using telecom network security software to manage cybersecurity in telecommunications offers real-time monitoring, automated threat detection, and streamlined compliance with industry regulations. It enhances network visibility, reduces manual errors through automation and accelerates incident response. This leads to improved security posture, operational efficiency, and effective risk mitigation in complex telecom environments.
Why Are Telecommunications Companies a Main Target for Network Attacks?
Telecommunications are a primary target for network attacks because they form the backbone of global communication and data exchange. Disrupting telecom networks can cause widespread service outages, access to sensitive information, and facilitate further cyberattacks. The vast, complex infrastructures offer multiple entry points, making them attractive to attackers aiming for maximum impact and exploitation of vulnerabilities.
How Does 5G Deployment Affect Telecommunications Network Security?
5G deployment significantly impacts telecommunications network security by increasing the attack surface with a higher number of connected devices, virtualized network functions, and edge computing. The complexity of 5G architecture introduces new vulnerabilities, requiring robust security measures such as real-time threat detection, automated policy enforcement, and continuous compliance monitoring.
Additionally, the transition to software-defined networking (SDN) and network slicing increases the risk of misconfigurations and cyber threats. Telecommunications providers must implement proactive security strategies to protect critical infrastructure, ensuring data integrity, service availability, and regulatory compliance in an evolving threat landscape.
What Compliance Standards Are Most Critical For Telecommunications Security?
Critical compliance standards for telecom security include GDPR for data privacy, PCI DSS for secure payment processing, NIST for cybersecurity best practices, and ISO 27001 for information security management. Additionally, FCC regulations in the U.S. and Telecommunications Security Act (TSA) in the U.K. impose strict security requirements. Compliance with CISA guidelines and ITIL frameworks further enhances security and risk management.
Given the evolving threat landscape, telecom providers must continuously assess and update their security policies to meet these regulatory standards and protect sensitive customer data.