Simple doesn’t scale. As organizations continue to adopt cloud services, security complexity increases exponentially. Managing compliance, maintaining inventory, tracking changes, reducing misconfigurations, all while handling threats and users is a massive challenge. Organizations need tools that support cloud security operations across decentralized cloud teams and operations.
FIREMON
Cloud Defense
Real-time cloud security compliance, inventory, misconfiguration, and threat detection.
Now with Just-In-Time IAM defense at an industry-best price.
Pragmatic CSPM for Security Operations
Sign up for our Free Enterprise Scale CSPM
Daily assessments and compliance reports with a 30-day resource inventory.
No account limits! (AWS and Azure available now)
FireMon Cloud Defense
Understand More:
FireMon Cloud Defense is designed to get you the information you need to understand your security and compliance risks, without flooding you with noise.
Communicate Better:
Our deep ChatOps integration is built to meet the needs of decentralized cloud operations. Issues are routed directly to the teams who can respond to them while keeping security in the loop.
Remediate Faster:
Our event-driven automation engine can fix issues automatically or use our ChatOps integration to embed guidance and 1-click actions for a human decision.

FireMon Cloud Defense Features
Real-Time Cloud Posture, Inventory, and Change Tracking
FireMon Cloud Defense natively monitors API activity in your cloud deployments, updates inventory, and runs security and compliance assessments in real-time to ensure nothing falls through the cracks.
- A searchable cloud asset inventory with a full change history including which IAM entity made the change
- Highly customizable real-time security assessments to detect misconfigurations based on the classification of the environment
- Continuous compliance tracking and reporting with environment filtering and compensating controls
- An intelligent issues feed integrated with inventory to direct you to the problems and resources that matter most

Cloud Native Threat Detection and Response
Instantly detect potential malicious activity and generate enriched alerts to help discern between external attacks, malicious insiders, or innocent mistakes.
- Cloud threat detectors that monitor real-time API activity to enhance your SIEM/monitoring
- Automatic enrichment, including resource and posture information, to speed up analysis and investigation
- Filter issues and alerts for different projects, deployments, and environments to reduce false positives and alert fatigue
- Improves your cloud provider’s native security alerts with integrated enrichment, filtering, and routing

Automated Cloud Security Maturity Model Assessments to Improve Your Security Program
Discover and quickly assess your cloud security readiness and identify steps to strengthen your security fortifications using Key Performance Indicators.
- Utilize the Cloud Security Maturity Model 2.0, developed by the Cloud Security Alliance, IANS, and Securorsis to automatically assess your cloud deployments
- Measure the maturity of your cloud security with automated assessments
- Insight into strengths, weaknesses, and opportunities for improvement across various security domains and categories
- Provides maturity ratings, control objectives, and KPIs to help you assess your maturity level and create a roadmap for improvement
- Compare different teams’ level of security maturity and prioritize areas that need attention

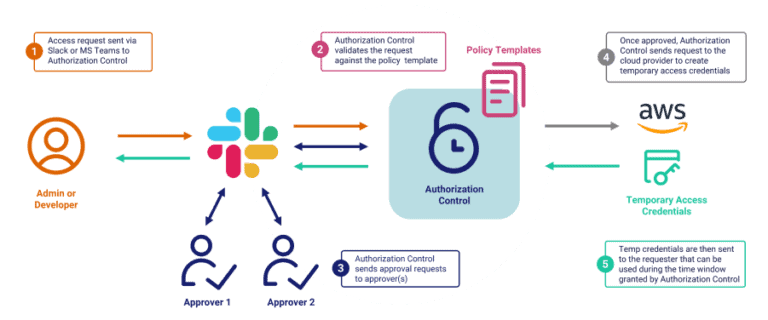
Authorization Control to Reduce Identity Risks
Eliminate the need for static credentials or long-term permissions with just-in-time approvals, out-of-band visibility, and session restrictions.
- Cloud threat detectors that monitor real-time API activity to enhance your SIEM/monitoring
- Automatic enrichment, including resource and posture information, to speed up analysis and investigation
- Filter issues and alerts for different projects, deployments, and environments to reduce false positives and alert fatigue
- Improves your cloud provider’s native security alerts with integrated enrichment, filtering, and routing

How Authorization Control Works
Deep ChatOps Integration to Bridge Silos
Bridge the communication gap between decentralized cloud operations teams, ensuring effective security across teams for rapid assessment, response, and remediation of misconfigurations and attacks.
- Full Slack and Teams support for notifications and actions
- Advanced routing so teams only see the issues regarding their deployments, while security still monitors everything
- Notifications are enriched with enhanced information and options for 1-click remediations right in the channel
- Security can easily coordinate with cloud teams in ChatOps for rapid investigation and response

Event-Driven Automation and Assisted Remediation
FireMon Cloud Defense uses an advanced, event-driven, serverless architecture to send notifications and take actions at the speed of your cloud platform.
- Alerts route instantly, appearing in less than 30 seconds on AWS or GCP and within 2 minutes on Azure
- Support for fully automated remediations that apply only to the deployments you designate
- All ChatOps notifications can include defined or recommended 1-click remediations to let an administrator make the decision
- Integrate with third-party systems to create tickets or trigger external workflows
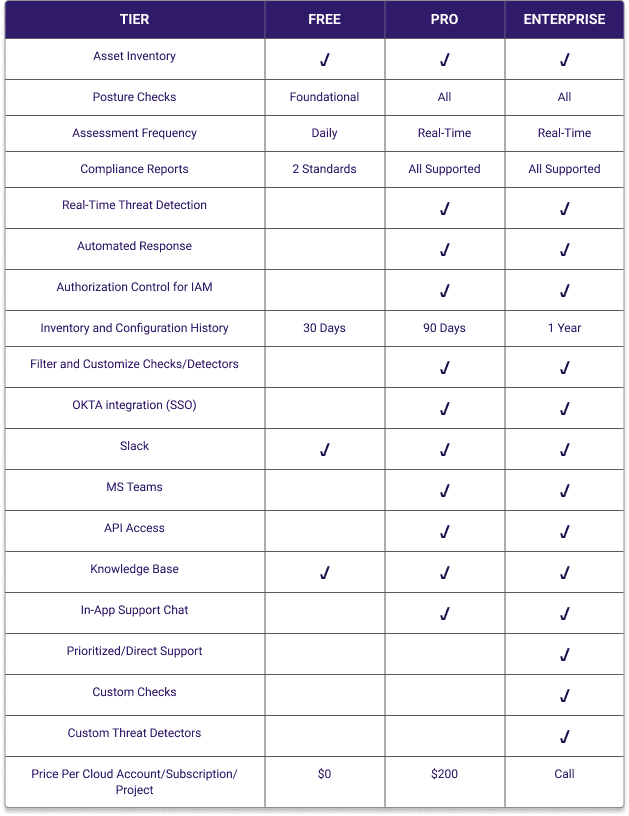
Cloud Defense Pricing
Simplified base pricing. FireMon also offers resource-based and other pricing models to align with customer preferred patterns.
Learn More About Cloud Defense
Try it for Free
See for yourself how Cloud Defense can protect your organization
Unlimited usage at no cost!
Sign Up Now
Thanks for signing up to use the FireMon Cloud Defense Tool. You’ll get an email soon - click the link in that email to create your account and set a password.