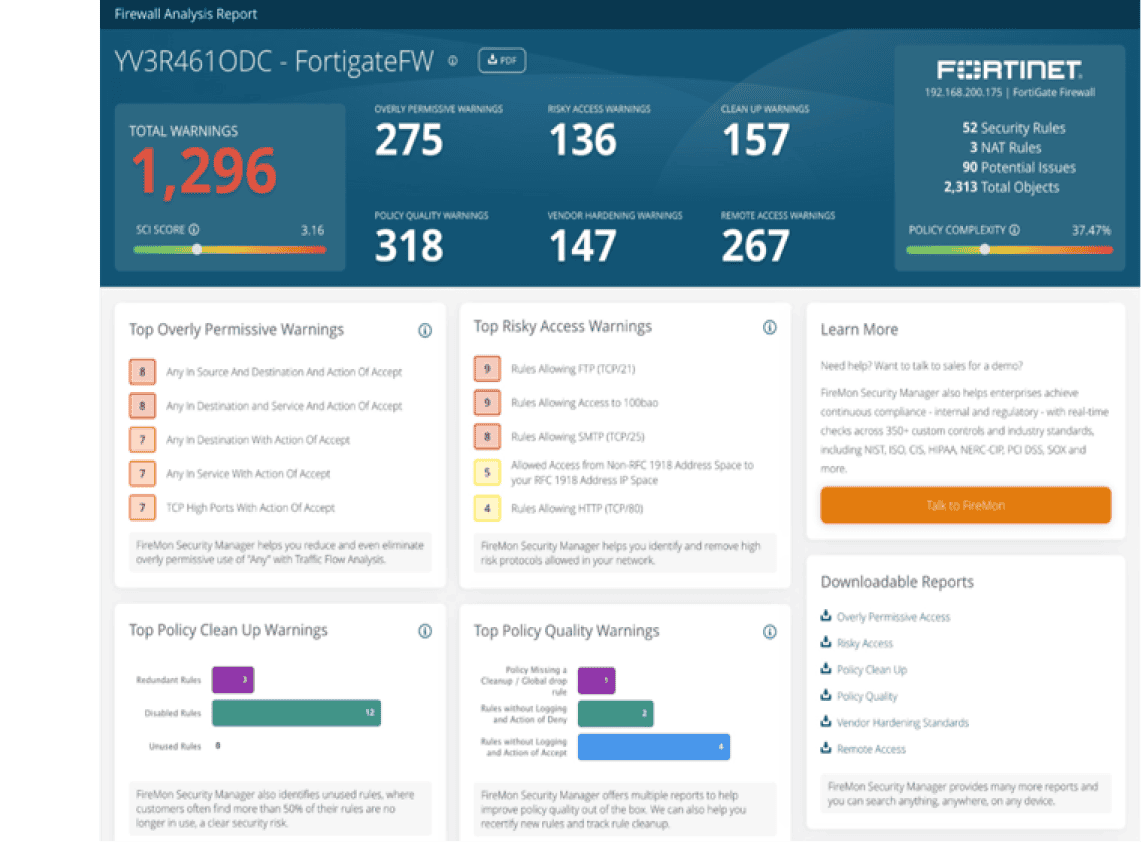
Firewall policy analysis is the process of evaluating and optimizing firewall rules and configurations to ensure they effectively protect the network. It involves reviewing policies for accuracy, real-time compliance, and efficiency, identifying redundant or conflicting rules, and ensuring alignment between your security compliance toolkit and industry best practices.
The analysis and insights from a firewall policy analyzer help enhance network performance, reduce vulnerabilities, and maintain regulatory compliance.
A robust policy analyzer ensures that firewalls remain effective against evolving threats, providing robust protection for the organization’s digital assets.