Why Choose FireMon for
IT Network Security Management?
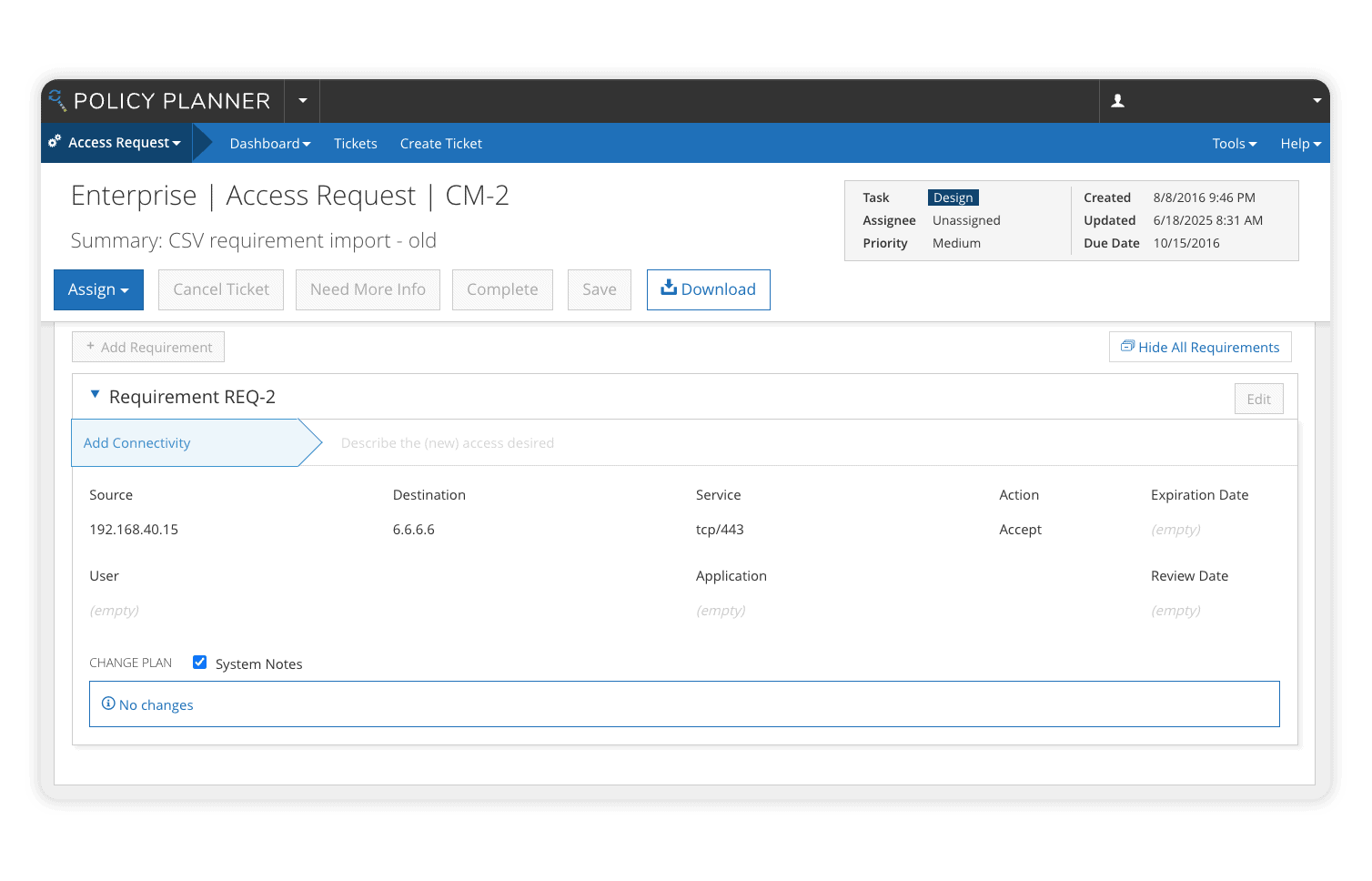
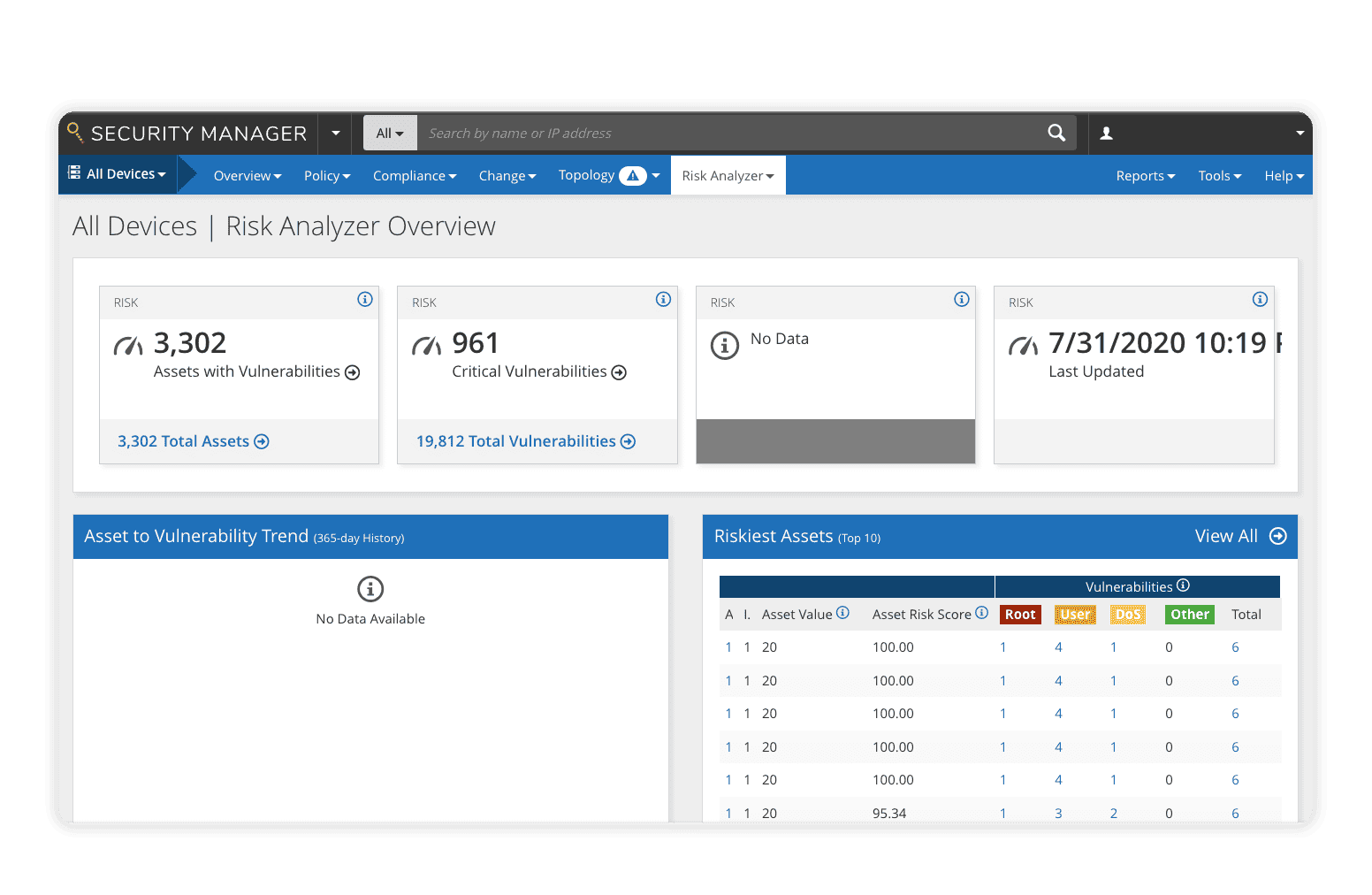
FireMon offers a comprehensive solution designed to address the growing complex security needs of modern networks. FireMon’s platform combines real-time monitoring, compliance management, and automated policy enforcement to deliver unmatched visibility and control over your network infrastructure.