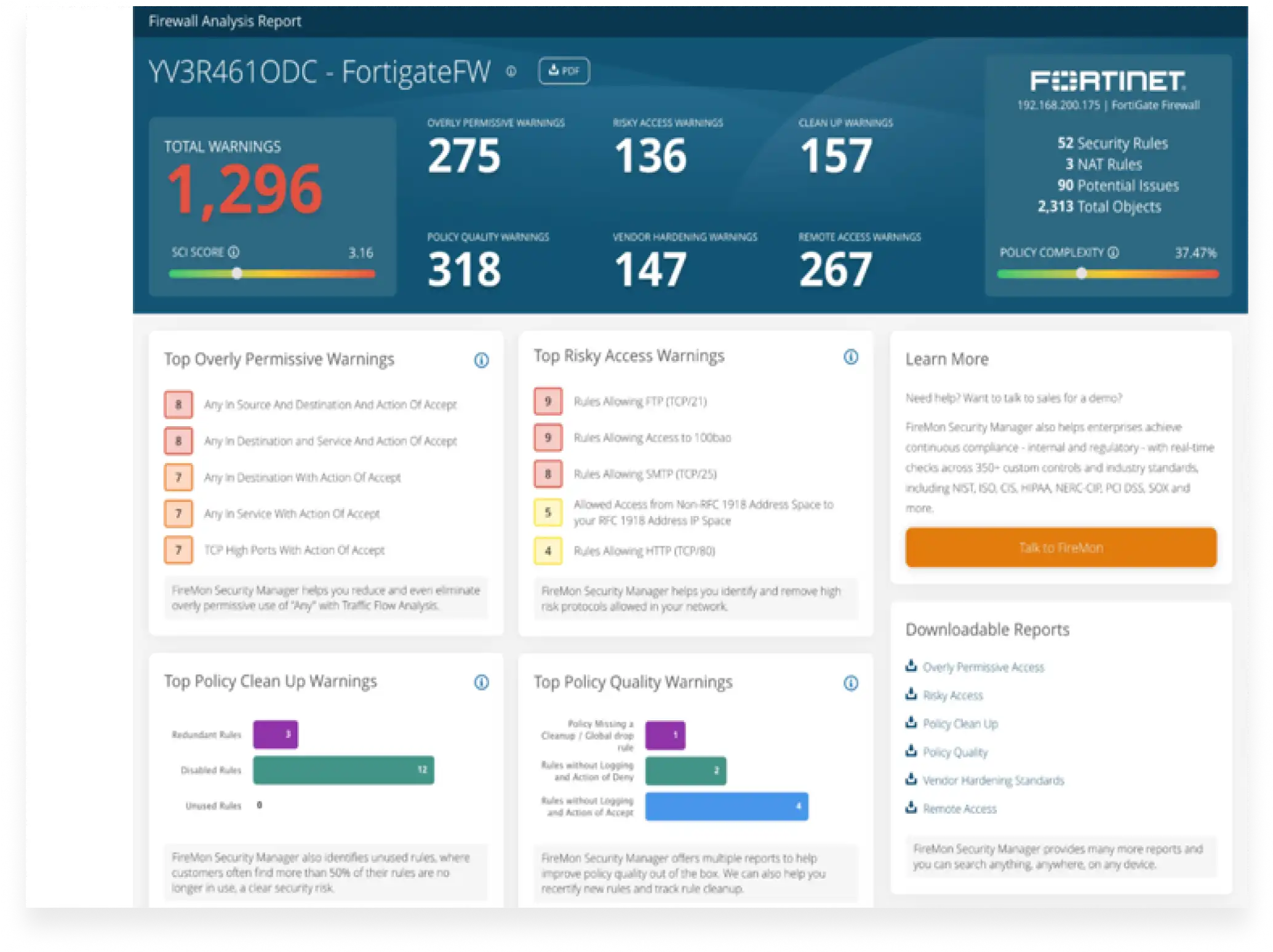
Correctly setting up a firewall is one of the most important things you can do to protect your enterprise network. While firewalls serve as the first line of defense, their effectiveness depends on proper configuration and continuous monitoring. An improperly set firewall can leave your network vulnerable to cyber threats, performance issues, and compliance risks.
This guide breaks down the essentials of enterprise firewall configuration, provides practical steps for securing your setup, and explains why continuous monitoring is key to long-term protection.
Key Highlights:
- A well-configured firewall safeguards sensitive enterprise data, improves network performance, and ensures regulatory compliance.
- Essential steps include implementing least-privilege access rules, enabling logging, and using automation to streamline monitoring and management.
Why Proper Firewall Setup Is Critical for Organizations
A firewall is a critical security barrier, but if it’s set up incorrectly, it will inevitably do more harm than good. Firewall misconfigurations leave gaps that cybercriminals can exploit, leading to:
- Increased risk of cyberattacks: An improperly configured firewall can expose sensitive data and make your network open to breaches.
- Regulatory non-compliance: Weak firewall settings can result in compliance failures, leading to fines or audit penalties.
- Performance issues: Poor configuration can create network bottlenecks, slowing down essential business operations.
- Higher costs: A data breach caused by a misconfigured firewall can lead to financial losses and damage your company’s reputation.
Human error vulnerabilities: Simple mistakes during setup or management can create security gaps. (Learn more in our guide on avoiding human error.)
The Effects of Firewall Misconfigurations
Firewall misconfigurations have been behind some of the most significant cyberattacks in recent history. Here are two major incidents that highlight why getting firewall settings right is critical:
Capital One Data Breach (2019)
In 2019, a misconfigured firewall allowed an attacker to access Capital One’s cloud-based infrastructure, exposing the personal information of more than 100 million people. This breach underscored the critical need for secure firewall rules to prevent unauthorized access.
Microsoft Power Apps Data Exposure (2021)
During the COVID-19 pandemic, a misconfiguration in Microsoft’s Power Apps platform resulted in 38 million records becoming publicly accessible. The issue stemmed from a default setting that required manual adjustments for privacy—highlighting the risks of relying on default configurations without active security management.
These cases demonstrate why enterprises must proactively configure and regularly audit their firewall settings to avoid similar security lapses.
How to Configure Firewall Settings for Your Network
Setting up a firewall correctly involves multiple steps to ensure your network remains protected. Follow these eight steps to build and maintain a secure firewall configuration.
1. Access Firewall Management
Start by accessing the firewall’s management interface, typically through a web-based GUI or command-line interface. Ensure administrative controls are locked down with strong passwords and access restrictions, allowing only authorized personnel to make changes.
2. Define Core Network Infrastructure Settings
Map out your network architecture, including IP ranges, subnets, and security zones. This helps align your firewall rules with your network’s structure, reducing the risk of unauthorized lateral movement within your environment.
3. Craft Firewall Ruleset and Policies
Establish clear inbound and outbound traffic rules based on the principle of least privilege. Only allow necessary connections, blocking everything else by default. For an in-depth approach, check out our guide on optimizing firewall rules.
4. Establish Logging and Monitoring Protocols
Turn on logging to capture firewall activity and track traffic patterns. Regularly reviewing logs as part of ongoing firewall monitoring helps you identify unusual behavior early and respond before threats escalate.
5. Implement Network Address Translation
Configure Network Address Translation (NAT) to mask internal IP addresses from external threats. This extra layer of security prevents attackers from mapping out your internal network and targeting vulnerable assets.
6. Configure Threat Detection and Prevention Controls
Activate security features like Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to detect and block suspicious activity. Many modern firewalls also include application-layer security to defend against advanced threats.
7. Validate Firewall Configuration Integrity
Conduct regular firewall reviews to catch misconfigurations before they become security risks. Look for open ports, overly permissive rules, and outdated policies that could expose your network to attacks.
8. Continuously Monitor and Validate Configuration
Security is an ongoing process. As such, implement ongoing firewall configuration monitoring to ensure configurations remain up-to-date, secure, and compliant.
Streamline Firewall Configuration Management with FireMon
Manually managing firewalls across an enterprise can be overwhelming, especially for large, complex networks. Tools like FireMon’s Policy Manager simplify firewall configuration management, offering centralized monitoring, policy optimization, and automated compliance checks. They also assist in conducting firewall compliance audits, ensuring your setup meets industry standards.
Book a demo today to see how FireMon can help you take control of your firewall security.
- Increase Visibility: Eliminate blind spots with a network security manager that gives a complete view of all firewall policies across the entire environment
- Reduce Risk: Remediate policy-related vulnerabilities with real-time visibility and control
- Manage Change: Avoid misconfigurations, accelerate business, and improve security
- Enforce and Maintain Compliance: Avoid violations, avoid risk, and avoid fines
Frequently Asked Questions
How Often Should I Review and Update Firewall Settings?
In short, your firewall review cycle should be as dynamic as your environment, quarterly at a minimum, but preferably continuous. The more proactive you are, the less reactive you’ll need to be when a security event occurs.You should review and update firewall rules at least quarterly, or sooner if there are major changes to your network. Frequent audits help eliminate outdated rules, optimize performance, and prevent security gaps. Automated monitoring tools can make this process faster and more efficient.
What Metrics Should I Track to Evaluate Firewall Performance?
When it comes to evaluating firewall performance, you need to track metrics that provide both security insights and operational efficiency. Firewalls aren’t just about blocking threats—they need to do so without bottlenecking your network. Here are the key metrics you should be monitoring:
- Packet Filtering Efficiency – This tells you how well your firewall is blocking malicious or unauthorized traffic while allowing legitimate traffic through. If too much bad traffic is slipping by, you have a problem.
- CPU and Memory Usage – Your firewall is a critical security tool, but it shouldn’t be overloading system resources. High CPU or memory consumption can slow down network performance and even cause outages.
- Throughput – Measures how much traffic your firewall can handle without dropping packets. If your business is growing and network traffic is increasing, you want to ensure your firewall keeps up.
- Latency – Your firewall should be adding minimal delay to network traffic. If users complain about slow connections, latency issues from an overloaded firewall could be a contributing factor.
- Alert Frequency & Response Time – How often is your firewall flagging security threats, and more importantly, how quickly are they being addressed? If you’re getting flooded with alerts but response times are lagging, it’s time to optimize your firewall rules and incident response workflows.
Tracking these metrics consistently will ensure your firewall remains an effective security asset while maintaining optimal network performance.
What Are the Key Differences Between Hardware and Cloud-Based Firewalls?
- Hardware Firewalls – These are physical appliances deployed within your network perimeter. They’re great for securing on-premises environments and providing granular control over internal traffic. However, they require ongoing maintenance, manual updates, and can be expensive to scale as your network grows.
- Cloud-Based Firewalls – Often delivered as a service (FWaaS), these firewalls are hosted in the cloud and designed for distributed, hybrid, and remote-first environments. They’re highly scalable, offer automatic updates, and are easier to manage across multiple locations. The tradeoff? You’re often relying on a third-party provider for configuration and uptime.