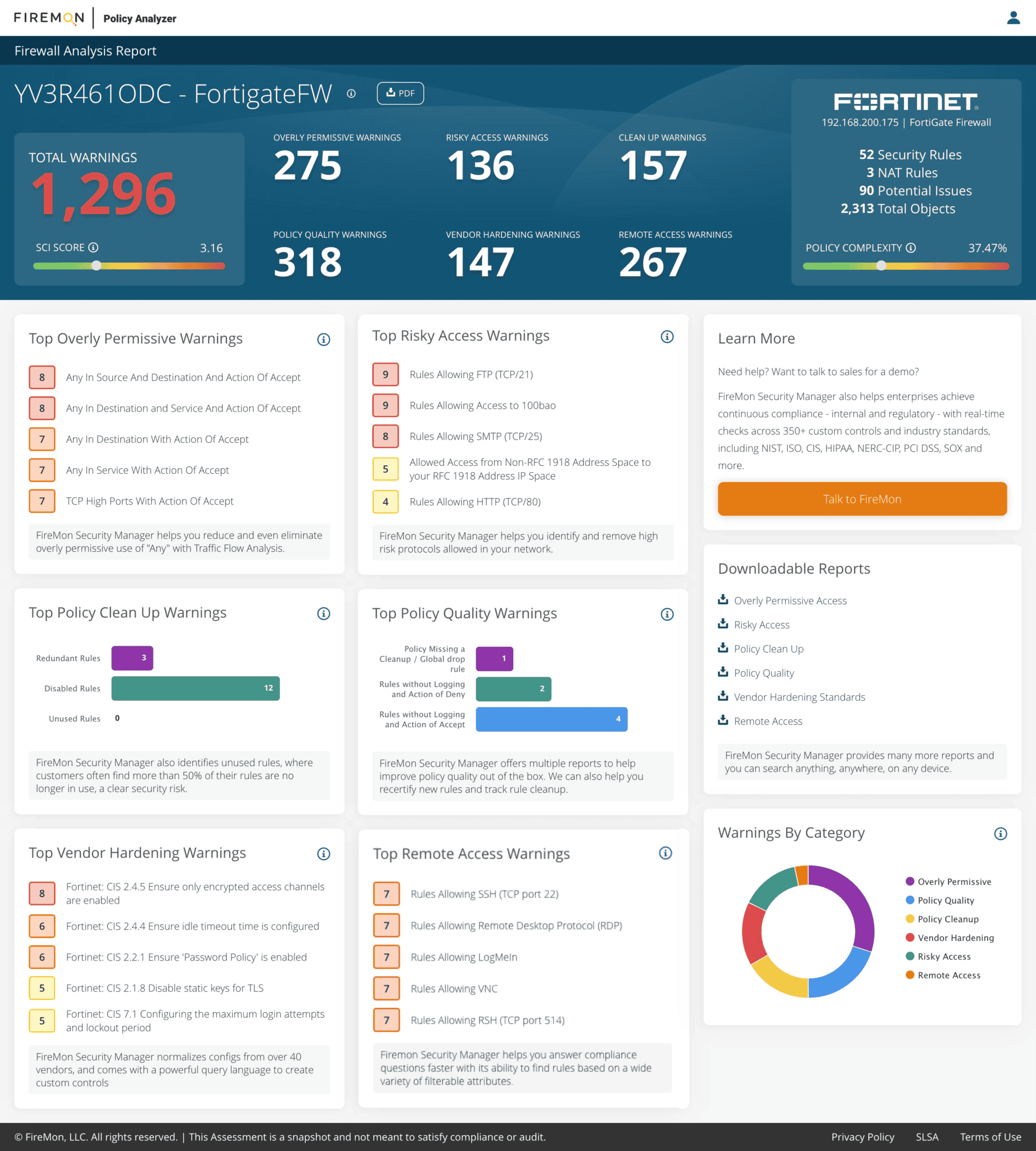
If you’re reading this blog, you’re likely interested in learning more about FireMon Policy Analyzer or have just run your first assessment and are curious how to get the most out of your results. Either way, we’re excited you’re here! As a reminder for those who aren’t familiar with Policy Analyzer, it’s a complimentary firewall security policy assessment solution that tests your firewall configuration and rulebase against FireMon’s best practices to reduce policy-related risk. Within minutes, Policy Analyzer shares a diagnostic report outlining the security posture of a single firewall in your environment, complete with key areas of interest and remediation recommendations. We encourage you to try it for yourself! So now you’ve run your first report but are curious where to begin. The dashboard provides a visual representation of the overall policy health within that particular firewall. The top of the report gives you a high-level view of the health of your firewall. It starts with the total number of identified warnings and a Security Concern Index (SCI) score, a device complexity score, and then displays six key results:
- Overly permissive warnings
- Risky access warnings
- Clean up warnings
- Policy quality warnings
- Vendor hardening warnings
- Remote access warnings