EXECUTIVE SUMMARY
Today’s threat landscape is constantly evolving. Sophisticated cyber threats are becoming smarter and faster, leading to an increase in security breaches and unprecedented fines for non-compliance. Simultaneously, organizations are rushing to drive increased business agility through digital transformation, embracing emerging technologies like mobility, cloud computing, largescale virtualization, software-defined networking, and the hyperconnected Internet of Things. Yet, organizations worldwide face an inability to hire and retain skilled security professionals, putting additional strain on lean security teams and increasing their security risk.
The result is a complexity gap where emerging network and cloud technologies outpace security teams’ ability to secure and manage their expandingenvironments perimeters, severely inhibiting business agility. Organizations find themselves at a crossroads – they must ensure that security doesn’t slow down innovation and that innovation doesn’t compromise security. Closing the complexity gap at scale requires automation of network security functions to replace manual, error-prone processes, maintain regulatory and internal compliance, and reduce overall security risk. This will increase the efficiency and efficacy of security teams, drive business innovation, enable business agility, and improve the bottom line.
This post describes how the complexity gap is impacting organizations and the pivotal role network security policy automation plays in helping organizations reduce risk and enhance their overall security posture.
The Bottom Line
Automation of key network security functions will provide much needed consistency and control across hybrid network environments required to reduce the complexity gap. It will enhance compliance efforts, reduce risk, and improve productivity for time- and resource-strapped security teams. As a result, organizations can improve their overall security posture, meet regulatory and internal compliance requirements, and achieve the business agility they need to keep up with the growing demands of the business.
Sidebar: Fast Facts
- The rapid pace of digital transformation demands error prone, manual network security processes be automated.
- It is increasingly difficult to maintain consistent, continuous compliance of network security devices from multiple vendors and eliminate costly misconfigurations caused by human error.
- Security policy enforcement points are not only a vital part of the network security architecture, they are growing in criticality as networks expand in scope and complexity across multiple environments.
- An intelligent network security platform will provide the automation and analysis capabilities needed to tame network sprawl and enable security practitioners to make better-informed decisions based on context and actionable intelligence.
- Centralized management is essential in order to provide real-time visibility and control over the hybrid network and a central policy enforcement point.
- Advanced analytics and security intelligence capabilities will enable better decision making and help detect, prevent, and proactively respond to threats.
Technology Sprawl Adds to Complexity
Hybrid networks have become increasingly complex, both in terms of the number of endpoints and technologies in use. The explosive growth in the number of mobile devices and the emergence of the Internet of Things (IoT) has massively accelerated endpoint proliferation. Cloud-based applications and services have also grown in popularity, driven by the flexibility, speed, and convenience they offer.
Sidebar: Cloud Adoption Outpacing Security – 60% of respondents say cloud business initiatives are accelerating faster than security teams’ ability to secure them.
Because organizations tend to use multiple security vendors in a hybrid cloud environment, they may be unintentionally, or intentionally, adding to the complexity of managing and securing their networks. The FireMon 2019 State of Hybrid Cloud Security report showed that 59% of respondents use two or more different firewalls in their environment, with 67% of those using two or more firewalls also using two or more public cloud platforms.
Figure 1: Network Complexity
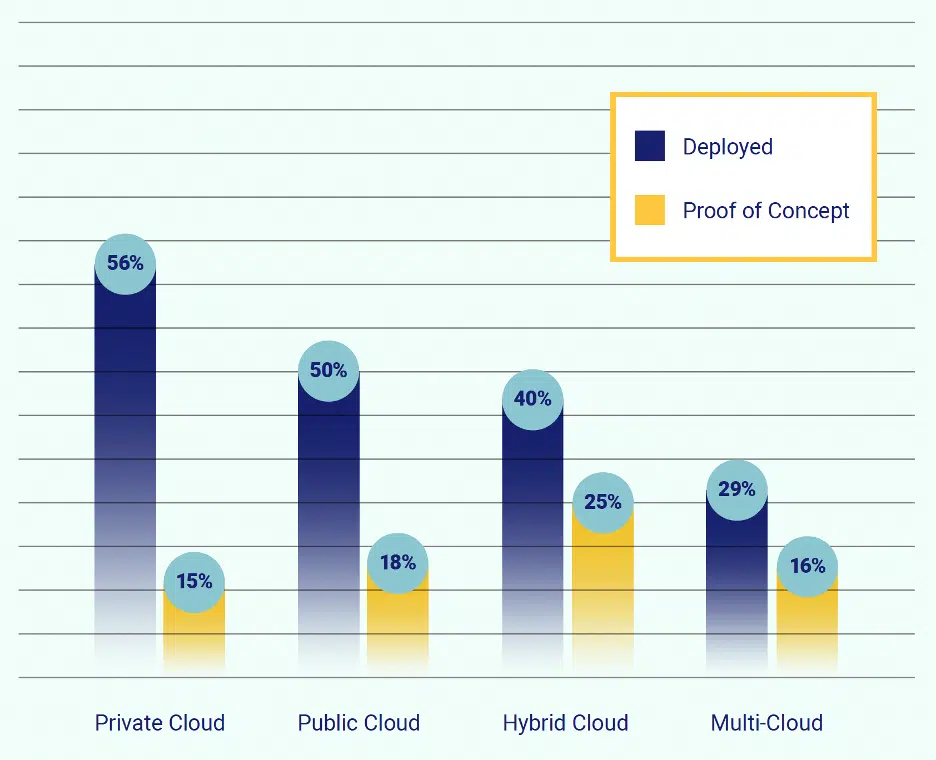
The proliferation of cloud throughout the enterprise has enabled enhanced business agility, but there is a concomitant increase in complexity that may offset those gains. Most businesses are already deployed in cloud environments, with 50% having two or more different clouds deployed, while 40% are deployed in hybrid cloud environments, and 23% have two or more different clouds in the proof of concept stage or are planning to deploy in the next 12 months.
Figure 2 – Technology Sprawl
Sidebar – Technology Sprawl Increases Complexity and Impedes Business Agility
1995 – Stateful, packet inspection firewall is introduced. Most organizations deploy only a handful of devices at the perimeter.
2001 – Impact of WAN, DMZs, and multiple ingress/egress points begins to increase device counts.
2005 – Virtualization and mobility, cornerstones of business agility, lead to erosion of the perimeter and proliferation of network segments.
2009 – Virtualized infrastructure combined with PCI-DSS standards drives more network segmentation.
2016 and beyond – Enterprises operate hybrid infrastructures and security begins to adapt through methodologies including, but not limited to, microsegmentation and containerization.
2019 – COVID-19 Pandemic causes rapid shift to work-from-home; organizations putting heavy load on distributed networks.
Limited Visibility Equals Increased Complexity
Increasing complexity reduces visibility across and into hybrid networks, making threats more difficult to identify and contain. Organizations that use multiple security tools across their physical and cloud environments may find that they lack a holistic view of their network infrastructure, hindering threat hunting efforts as well as prioritization of remediations. According to EY, 77% of organizations are still operating with only limited cybersecurity and resilience. They may not even have a clear picture of what and where their most critical information and assets are — nor have adequate safeguards to protect these assets.
Lack of network visibility is also problematic for organizations who cannot manage and patch devices that have not been detected. These unknown devices increase the probability of leak paths, which can cause corresponding policy or segmentation violations. Leak paths also include unauthorized or misconfigured internet connections from any part of an enterprise network—including the cloud—that allow traffic to be forwarded to a location on the internet. Leak paths can be especially hard to detect in cloud environments, where there is less network visibility and fewer security controls.
Shortage of Security Skills Creates an Abundance of Complexity
Adding to the challenge of improving an organization’s security posture is the lack of qualified security personnel. Though the number of unfilled cybersecurity job openings actually dropped for the first time in years in 2021, it still stands at nearly 3 million. Organizations will continue to see their security teams being asked to do more with less, with no relief in sight.
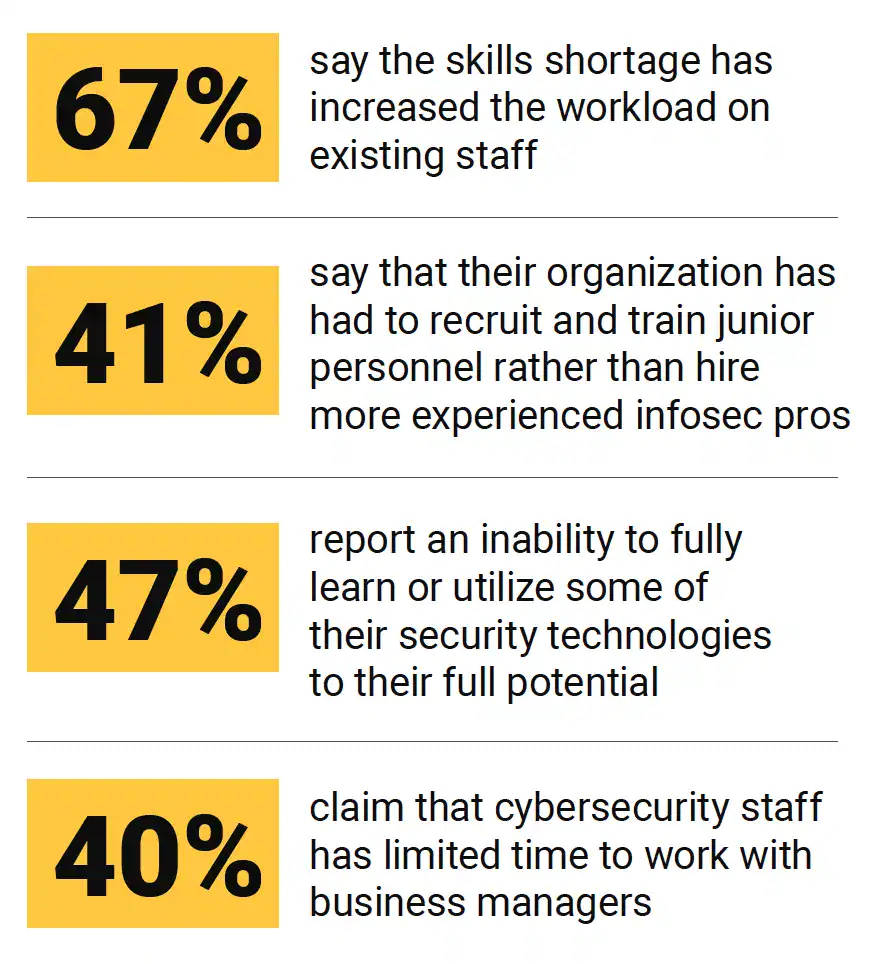
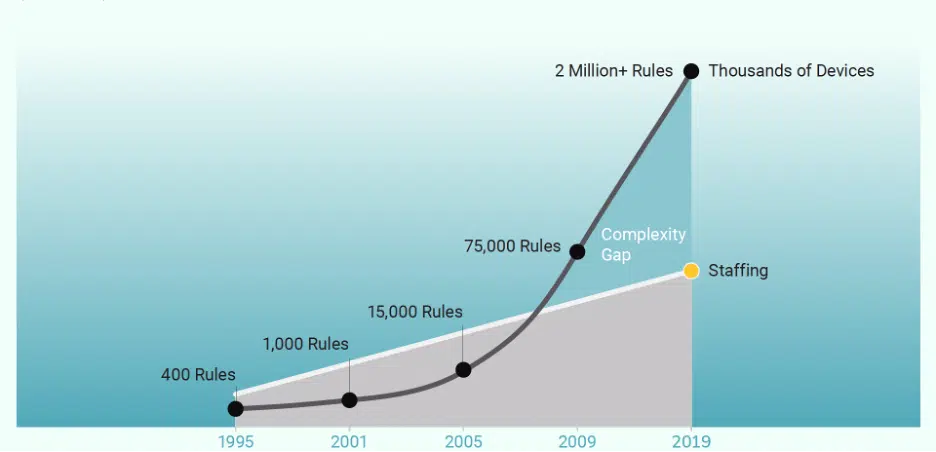
A cooperative research project by ESG and ISSA showed that one-third of survey respondents (as shown in Figure 3) believe that the global cybersecurity skills shortage has had a significant impact on their organizations, while 41% say the skills shortage has impacted their organizations somewhat. In addition, a three-year research trend clearly indicates organizations are not improving their ability to deal with the cybersecurity skills shortage. Increasing technology sprawl and the lack of availability of skilled personnel has created a complexity gap, as shown in Figure 4. The number of devices and associated rules has risen exponentially over the years, while the number of skilled staff has not.
Figure 3 – The Cybersecurity Skills Shortage Impact
Figure 4 – The Complexity Gap
Automation is Essential
Given the growing complexity gap caused by all these factors, automation is essential. Manual processes are time-consuming and error-prone. Misconfigurations have become the main culprit in firewall and cloud breaches as understaffed security teams struggle with too many tools, lack of proper training, and policy complexity. According to FireMon’s 2019 State of the Firewall Report, 65% of respondents still utilize manual change management processes despite high volumes of change requests. Some 36% of respondents report that more than 10% of their network changes require rework due to inaccuracies or issues on the network, mostly driven by human error.6 Ultimately, the lack of automation can result in compliance violations, increased risk, and unplanned outages that can hinder business operations.
As the agility of cloud computing accelerates innovation for DevOps teams, it also increases an organization’s potential threat surface. While the importance of security has driven some efforts to shift security left, many DevOps teams have had to sacrifice security for innovation. The 2019 DevSecOps Community Survey found that 48% of developers continue to believe security is important, but don’t have enough time to spend on it.
Network security devices such as firewalls must be able to manage continuous churn and change quickly as new users, applications and devices are granted access. Additionally, they must be able to quickly revoke access as business needs change. Access rights that remain in effect when no longer needed present a significant security risk to the organization.
Figure 5 – How Organizations are Utilizing Automation for Change Management
A major problem in managing firewall deployments, especially on a large scale and across on-prem and hybrid environments, is achieving visibility into policies that govern rule sets. Lack of comprehensive visibility makes it difficult to identify rules that are redundant, hidden, shadowed, outdated, or overly permissive.
A lack of automation is decreasing business agility by tying up many teams who could be working on other crucial projects instead of routine requests, as shown in Figure 7. 72% of respondents have two or more teams involved in processing and/or approving a typical change request. And of the 72% with two or more teams involved, almost 30% of them have three teams involved in processing and/or approving a typical change request. This points to a clear case for replacing manual tasks with automation to eliminate process bottlenecks.
In addition, as shown in Figure 4 “The Complexity Gap,” not only has the number of devices in use expanded over the years, but the number of rules governing their configuration has skyrocketed. In 2021, a large enterprise may see upwards of two million rules in use, up from just some 400 when firewalls came into regular use in the mid-1990s.
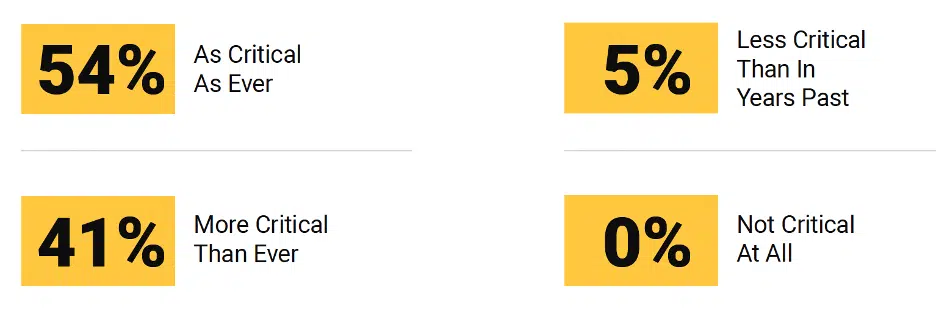
Figure 6 – Criticality of Network Firewalls
Requirements of Automated Network Security Policy Management
Maintaining a robust security posture is necessary to protect the hybrid network environment from security threats and incidents; achieve audit and compliance requirements; and set the foundation for enabling innovation without compromising security. By automating network security policy management, organizations can reduce security errors, standardize simplify workflows, and make security an enabler to achieve their business objectives.
- A primary requirement of an automated network security policy management platform is realtime and comprehensive visibility across the entire network infrastructure, including on premise, private cloud, and public cloud. Centralized management through a single pane of glass must provide the visibility needed into the rules associated with network security devices to determine the state of an organization’s current configuration, evaluate the effectiveness of security policies, and scope the impact of any proposed policy changes on an organization’s compliance and security posture. Advanced analytics capabilities help security teams plan and monitor the effectiveness of security policies.
- An automated network security policy management platform will provide a centralized point to determine which policies can be enforced to eliminate unnecessary access and security risk. Through comprehensive rule analysis and simplified automated workflows, organizations can remove technical mistakes and misconfigurations, remove unused access, review and refine access to optimize the performance of network devices, reduce policy complexity, and enhance security posture.
- Another requirement of an automated network security policy management platform is the flexibility to scale automation to an organization’s specific requirements. Robust, open application programming interfaces (APIs) will accommodate an organization’s changing infrastructure and security demands and incorporate the critical information necessary to perform conclusive analysis of network security devices, policies and underlying risks.
Summary
As organizations seek to drive increased business agility by leveraging technologies like cloud computing, virtualization, software-defined networking, and the hyperconnected Internet of Things (IoT), they are also dealing with an inability to hire and retain skilled security professionals. This results in a complexity gap where digital transformation is moving faster than the ability of security teams to secure and manage it.
To overcome the complexity and achieve sustainable business agility, automation is essential. Deploying a network security policy management platform that automates manual functions and simplifies workflows will reduce misconfiguration errors and risk exposure and enable greater productivity for resource-strapped security teams. With automation, DevOps and SecOps can work in tandem to meet and maintain their compliance requirements, strengthen their security posture, and keep up with the growing demands of their business.