Artificial intelligence (AI) is revolutionizing the way enterprises approach network security. With cyber threats evolving at an unprecedented rate, businesses may consider implementing AI-driven security solutions to optimize resources and enhance their existing automated security processes. Network security that leverages this technology enables organizations to identify threats faster, improve incident response, and reduce the burden on IT teams.
Let’s review the benefits of AI network security to help maintain your enterprise’s posture and walk through the steps to integrate it within your current processes.
Key highlights:
- AI network security enhances enterprise threat detection, incident response, and risk management.
- Automated security solutions powered by artificial intelligence reduce false positives and improve operational efficiency.
- FireMon Insights leverages AI-powered intelligence to streamline security policy management and compliance.
- Continuous monitoring and intelligent automation strengthen network resilience against evolving cyber threats.
How Is AI Used in Cybersecurity?
Artificial intelligence and cybersecurity work hand-in-hand, giving security teams an edge in detecting, analyzing, and responding to threats in real time. Cyberattacks are evolving too fast for traditional methods to keep up, but AI network security helps bridge the gap. It learns from past incidents, recognizes emerging threats, and adapts as the attack landscape shifts.
Rather than replacing security teams, the tech acts as a force multiplier—automating routine tasks, filtering out noise, and surfacing the threats that actually matter. It’s not just about working faster; it’s about working smarter.
Threat Detection and Prevention
AI in network security is particularly good at spotting patterns, especially the subtle ones that hint at malicious behavior. Instead of relying on predefined signatures, it can recognize emerging threats by analyzing vast amounts of network traffic and identifying deviations from normal activity.
For example, if an attacker is probing a network with small, carefully timed scans to avoid triggering traditional detection systems, AI can still pick up on the anomaly and flag it as suspicious. That kind of proactive detection makes AI invaluable in preventing data breaches and unauthorized access.
Incident Response and Recovery
Speed matters when responding to a breach. AI-driven network security management tools accelerate incident response by automating the process of identifying, containing, and mitigating threats.
Instead of relying on security teams to sift through endless alerts, using artificial intelligence in cybersecurity can prioritize incidents and even take predefined actions—such as isolating an infected system—before an analyst even logs in. Beyond the immediate response, AI is also useful in forensic investigations, helping security teams reconstruct attack timelines and identify vulnerabilities that need fixing.
Behavioral Analysis
Some of the most dangerous threats don’t come from malware—they come from within. Compromised credentials, insider threats, and social engineering attacks can be hard to detect using traditional methods. AI helps by continuously monitoring user behavior and network activity to flag anomalies.
Say an employee logs in from an unusual location or downloads a massive amount of data outside of business hours — AI can spot the deviation and issue an alert. It’s not about catching false positives; it’s about providing context and helping security teams focus on real risks.
Reducing False Positives
If every minor anomaly triggered an alert, network security teams would drown in notifications. AI helps cut through the noise by refining security alerts and distinguishing between real threats and harmless activity.
By learning from past incidents, AI improves over time, reducing unnecessary alerts and allowing analysts to focus on what really matters. The result? More efficient security teams, fewer wasted hours, and a faster response to actual threats.
How Does AI Affect Automation Enterprises Currently Leverage?
Automation has long been a part of cybersecurity, but AI network security takes it to another level. Instead of following rigid scripts, it introduces intelligence and adaptability—allowing security teams to automate complex processes without losing control.
Here’s how AI changes the game:
| AI’s Impact on Enterprise Automation | ||
|---|---|---|
| Automation Aspect | Traditional Approach | AI-Enhanced Approach |
| Threat Detection | Relies on predefined signatures, often missing novel threats | Uses pattern recognition to detect unknown threats |
| Incident Response | Requires manual intervention, delaying reaction times | Artificial intelligence automates responses, reducing reaction times |
| Compliance Monitoring | Periodic manual audits | AI-driven continuous compliance ensures real-time security |
| Firewall Policy Management | Static rules require manual updates | Dynamically adjusts policies as threats evolve |
Benefits of Implementing AI for Network Security and Monitoring
Good posture isn’t just about having the best tools — it’s about staying ahead of attackers. AI for cybersecurity helps by providing smarter detection, faster response times, and better visibility into network activity.
Improved Threat Detection
AI-powered network security monitoring tools are particularly effective at spotting subtle threats that traditional methods might miss. AI enhances detection by identifying anomalies, analyzing historical attack data, and integrating with security intelligence systems. By continuously adapting to new threats, AI ensures enterprises stay ahead of evolving cyber risks.
- Identify Anomalies: Detect suspicious deviations in network behavior, whether it’s an unusual login, data exfiltration attempt, or lateral movement.
- Use Predictive Analytics: Analyze historical attack data to anticipate potential future threats.
- Provide Real-Time Threat Intelligence: Work alongside SIEM systems to continuously monitor and respond to evolving risks.
Enhanced Incident Response
Quick, decisive action is critical when responding to cyber threats. Artificial intelligence automates and accelerates threat mitigation, reducing response time and improving containment. By analyzing attack patterns and providing security teams with actionable insights, AI ensures incidents are addressed efficiently with minimal disruption.
- Automating Threat Mitigation: Executing containment actions without waiting for human intervention.
- Reducing Detection and Response Time: AI significantly shortens the time it takes to identify and remediate threats.
- Supporting Decision-Making:Providing context and recommendations to help analysts take swift, informed action.
Reduced Operational Costs
Cybersecurity operations can be resource-intensive, often requiring large teams to monitor, analyze, and respond to threats. AI reduces this burden by automating repetitive security tasks, improving network efficiency, and preventing costly breaches. With this technology, enterprises can optimize resources while maintaining strong security defenses.
- Reducing the Need for Large Security Teams: Automating repetitive tasks and allowing teams to focus on high-impact work.
- Optimizing Network Performance: Identifying inefficiencies and reducing unnecessary bandwidth usage.
- Preventing Costly Breaches: Proactively detecting and mitigating threats before they lead to major financial or reputational damage.
Strengthened Compliance Management
Keeping up with changing regulations can be a challenge for enterprises. AI simplifies compliance by automating security controls, identifying risks, and generating real-time reports. With automated compliance tracking, organizations can proactively manage security policies and avoid regulatory penalties.
- Automated Compliance Tracking: Ensuring security controls align with frameworks like GDPR, HIPAA, and PCI DSS.
- Identified Risk Areas: Pinpointing compliance gaps before they become violations.
- Simplified Audits: Providing real-time compliance reports to streamline the audit process.
Increased Visibility and Monitoring
Gaining complete visibility into network activity is essential for detecting and mitigating security threats. AI-powered monitoring continuously analyzes traffic, detects anomalies, and enhances threat investigation capabilities. With AI-driven insights, security teams can proactively detect and neutralize potential risks.
- Continuous Surveillance: Keeping an eye on network traffic, user activity, and endpoints 24/7.
- Behavioral Analytics: Detecting deviations in user behavior that could indicate insider threats.
- Forensics & Threat Hunting: Helping analysts investigate past incidents and refine security strategies.
Steps to Implement Cybersecurity AI
Cybersecurity AI is powerful, but rolling it out effectively requires careful planning. It’s not just about plugging in a security tool and hoping for the best. Successful implementation means embedding AI throughout your security strategy, ensuring it operates ethically, and continuously refining it to keep up with evolving threats.
Here’s a practical roadmap for integrating AI into your cybersecurity approach while keeping security, compliance, and human oversight at the forefront.
1. Integrate Security Throughout the AI Lifecycle
Models are only as secure as the systems they’re built on. If security isn’t part of the AI development and deployment process from the start, vulnerabilities can creep in—sometimes in unexpected ways.
From day one, organizations should incorporate secure coding practices, conduct regular security audits, and implement adversarial testing to ensure AI models can withstand attacks. Cybersecurity tools must be just as hardened against threats as the networks they protect. The earlier security is baked into AI workflows, the fewer surprises down the road.
2. Develop Threat Models and Risk Assessments
AI brings speed and scale to cybersecurity, but that only works if you understand what threats you’re defending against. A strong security strategy starts with threat modeling — mapping out potential attack vectors, vulnerabilities, and weaknesses in your environment.
Risk assessments that leverage AI can analyze massive datasets to detect patterns, anticipate threats, and prioritize security measures based on likelihood and impact. The result? A proactive defense that helps security teams stay ahead of emerging threats instead of just reacting to them.
3. Ensure Data Quality and Privacy
AI is only as effective as the data it learns from. If your AI model is fed biased, outdated, or poor-quality data, you’ll end up with unreliable results—and in cybersecurity, bad intel can be dangerous.
To get the most out of AI, organizations need strong data governance policies. That means ensuring models process clean, relevant, and unbiased data while maintaining strict privacy controls. Encryption, anonymization, and access restrictions should be standard to protect sensitive information. Compliance with data regulations like CCPA isn’t just about avoiding fines — it’s about maintaining trust and reducing exposure to legal risks.
4. Automate Detection and Response
One of the biggest advantages of cybersecurity and artificial intelligence working in tandem is speed. Automated systems can analyze vast amounts of network traffic in real time, flag anomalies, and, when necessary, take immediate action to contain threats.
With AI-driven security orchestration, teams can automate responses to common threats—such as isolating infected endpoints or blocking malicious traffic—without waiting for human intervention. This not only shortens response times but also reduces the workload for security teams, letting them focus on complex, high-priority threats.
5. Maintain Human Oversight and Collaboration
AI is an incredible force multiplier, but it’s not infallible. It works best when paired with human expertise. Security teams should work alongside tools, validating insights, analyzing complex threats, and making judgment calls that the technology simply isn’t capable of.
The best approach is a collaborative one—where AI handles high-volume, repetitive tasks, and human analysts focus on strategic decision-making. AI is a tool, not a replacement.
6. Adopt Ethical and Regulatory Frameworks
Automated policy management isn’t just about stopping attacks — it also has to be deployed responsibly. Organizations must ensure their AI systems align with ethical guidelines and comply with regulatory requirements.
That means maintaining transparency in security decisions, ensuring fairness in risk assessments, and following governance frameworks to prevent misuse. Compliance with industry standards like NIST, GDPR, HIPAA, and PCI DSS helps organizations avoid legal pitfalls while maintaining a strong security posture.
7. Continuously Monitor and Update Models
Cyber threats are constantly evolving, and so should your models. AI-driven security tools aren’t “set it and forget it” solutions—they require ongoing monitoring, tuning, and updates to remain effective.
Organizations need to refine their algorithms, retrain models with fresh data, and continuously test their AI systems against new and emerging threats. The best security strategies are dynamic, adapting alongside the very threats they’re designed to stop.
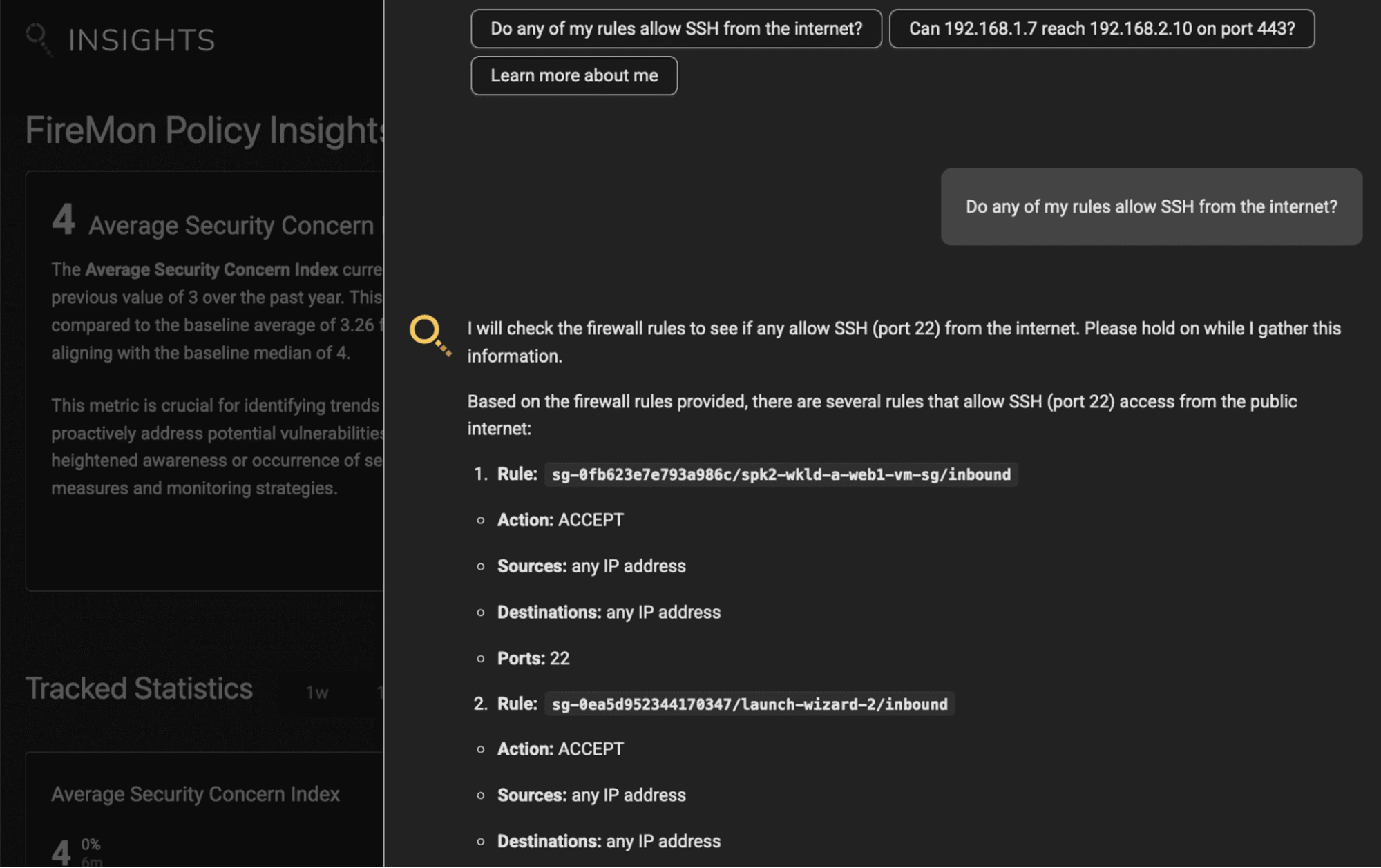
Streamline Security with the AI-Powered Intelligence of FireMon Insights
Effective AI network security requires continuous policy optimization, risk assessment, and compliance monitoring. FireMon Insights equips cybersecurity leaders with the tools they need to take control of their firewall policy management and answer critical questions about the effectiveness of their security efforts.
- AI-Driven Insights: Powered by nearly 50 KPIs and enriched with benchmarking and trending data, our AI engine identifies and prioritizes critical areas of concern.
- AI-Chatbot: Simplify firewall management with natural language interactions, enabling instant troubleshooting, policy validation, and insights.
- Trending Metrics: Track KPI progress over time to evaluate whether your management practices are driving improvement.
- Peer Benchmarking: Compare your organization’s firewall policy KPIs with industry peers to identify areas of weakness and potential risk.
Book a demo today and explore how FireMon’s AI-assisted Insights can help your security hygiene.
Frequently Asked Questions
Can Using Artificial Intelligence in Cybersecurity Replace My Current Processes?
No, and it shouldn’t. AI isn’t a silver bullet, it’s a force multiplier. It enhances existing security processes by improving detection, reducing false positives, and automating response workflows, but it doesn’t replace the need for human oversight or established security frameworks. AI is excellent at identifying patterns in massive datasets, spotting anomalies, and streamlining repetitive tasks, but it still lacks the intuition, strategic thinking, and nuanced decision-making capabilities of a skilled security team.
The best approach is to integrate AI-driven tools into your existing security stack to optimize efficiency while maintaining human control where it matters most, such as incident response, policy enforcement, and risk management. AI should complement and refine your security operations, not replace them.
What Are Common Use Cases for AI Network Security?
AI transforms network security in several key areas, primarily through automation, predictive analytics, and real-time response. Some of the most impactful use cases include:
- Threat Detection & Anomaly Recognition: AI continuously analyzes network traffic, identifying deviations from normal behavior that may indicate a cyberattack. Unlike traditional signature-based detection, AI can flag zero-day threats and sophisticated attack patterns before they escalate.
- Behavioral Analytics: AI-driven monitoring detects unusual user activity, such as abnormal login locations, access attempts outside regular hours, or deviations from typical workflows. This proactive approach is critical for spotting insider threats and credential-based attacks.
- Incident Response Automation: AI accelerates containment and mitigation by automatically triggering predefined response actions when a threat is detected, minimizing dwell time and reducing the workload for security teams.
- False Positive Reduction: Security analysts are often overwhelmed by alert fatigue. AI refines and prioritizes security alerts, distinguishing between genuine threats and benign anomalies so that teams can focus on real risks.
- Compliance & Risk Management: AI helps automate continuous compliance monitoring, flag policy violations and ensure that security controls align with regulatory requirements.
How Can I Select the Best AI Tools for Network Security?
Choosing the right AI tools for network security requires careful evaluation of several factors to ensure they align with your organization’s needs and risk profile. Here’s what to consider:
- Accuracy & Reliability: AI models vary in effectiveness. Look for solutions with proven accuracy in real-world threat detection, preferably backed by case studies, independent testing, or peer benchmarking.
- Ease of Integration: AI should work seamlessly within your existing security ecosystem, including SIEM, SOAR, firewalls, and endpoint security tools. Compatibility with your current infrastructure is crucial.
- Explainability & Transparency: Avoid “black box” AI solutions that lack visibility into how they make decisions. AI-driven security tools should provide clear, interpretable insights rather than vague risk scores.
- Automation vs. Human Oversight: Strike a balance between automation and manual control. AI should handle repetitive, high-volume tasks but allow security teams to intervene when necessary.
- Scalability & Adaptability: Ensure the AI model can scale with your enterprise’s growth and adapt to evolving threats. Machine learning-driven solutions should continuously refine their threat models based on new attack patterns.
- Compliance Capabilities: If your industry is subject to regulatory requirements, choose an AI tool that aligns with relevant security frameworks and compliance mandates.