Manual management of network security policies, rules, and configurations is time-consuming and error-prone, which adds operational cost and increases security-related risks — especially as your IT infrastructure grows more complex. Aberdeen’s analysis quantifies the value of a policy management solution, in both dimensions.
How your network security policies are managed affects both operational cost and security-related risk
Your organization’s network firewall infrastructure is probably not viewed as the shiniest new tool in its cybersecurity toolbox. Important, yes, but perhaps somewhat taken for granted — after all, it’s been roughly 30 years since the first commercial network firewalls were introduced. For this reason, it may not be well understood that how your network security policies are managed significantly affects both your operational cost and your security-related risk.
To illustrate this point: In an analysis of more than 13,000 network firewall installations, Aberdeen discovered a surprising degree of complexity. Nearly half (46%) of all enterprises in this market snapshot are characterized by multiple sites and / or multiple firewall vendors. In turn, each of these has numerous security policies, rules, and configurations that must be established, implemented, and maintained over time. This complexity can have serious consequences, including:
- Network security policies and rules may be conflicting, out of date, redundant, or the result of ad hoc decisions that bypassed the normal approval process.
- Policy configurations may be incorrect or out of date, whether from unapplied patches and updates or from routine human error.
Adding to the above is the complexity of evolving deployment models for an organization’s business-critical application workloads. Over the past few years, these workloads are increasingly executed on the computing infrastructure that best addresses the organization’s current requirements for performance, reliability, cost, geographic location, trust level, security, and compliance. On the plus side, these trends have led to tremendous agility for the business — but also to a complex, hybrid mix of enterprise-managed infrastructure (i.e., on-premises) and cloud service providers.
SIDEBAR: Security teams and business leaders should not be complacent about how their network security policies are managed. For many enterprises, IT infrastructure have grown surprisingly complex—adding significant operational cost and increasing security-related risk. The integration, visibility, and automation provided by leading security policy management solution providers can help win back control in both important dimensions. For the illustrative enterprise in this report, use of a security policy management solution resulted in an annual ROI of 4.3 times in terms of cost savings, and 2.5 times in terms of reducing security risks.
If network security policies are managed manually (or with multiple, inconsistent tools), the complexity of multiple sites, vendors, devices, policies, rules, configurations, and application deployment models has a ripple effect on both operational cost and security-related risk:
- Operational cost: Increased complexity corresponds to a non-linear increase in the operational cost of managing network security policies, rules, and configurations throughout the enterprise, based on the longer time it takes to review, check, approve, implement, test, and validate these adds or changes. Simply put, complexity requires more time and more technical staff.
- Security-related risks: In turn, greater complexity contributes to an increased likelihood of inconsistencies, errors, and omissions in these management tasks — which increases the number of threats and vulnerabilities that are relevant to the organization’s network infrastructure and network-dependent resources. Simply put, complexity increases the likelihood that these vulnerabilities may be successfully exploited, along with the corresponding business impact.
In this context, automation of the workflows for network security configuration changes and policy updates is increasingly essential — and is designed to provide a high level of assurance that these important tasks are accurately and consistently carried out. In addition, leading security policy management solutions provide continuous, real-time visibility into the actual policies, rules, and configurations that are currently in place throughout your network security infrastructure and ensure the necessary integration with a wide range of network firewall products and application deployment models.
Sidebar: Monte Carlo Models and Risk
In a Monte Carlo analysis, each variable in a calculation is expressed not as a single, static value — but as a range (lower bound, upper bound) and a shape (probability distribution). The relevant calculations are then carried out based on a randomly selected value from the probability distribution for each variable, over many (say, 10,000) independent iterations.
In doing so, the results of the analysis are also expressed as a range and distribution (as opposed to as a single, static value). The results can then be represented in terms of both how likely and how much impact — i.e., in terms of risk, as risk is properly defined.
This approach provides IT and Security professionals with exactly what they need to quantify estimates that are actually useful for making better-informed business decisions about risks, in spite of the inherent uncertainties in these matters. It also provides a useful tool for addressing fundamental business questions such as:
- The operational cost and security-related risk of managing network security policies manually
- The value of an incremental investment in a security policy management solution, for reducing operational cost (cost savings) and decreasing security-risk (cost avoidance)
Quantifying the operational cost and security-related risk of managing your network security policies manually
To quantify the operational cost and security-related risk of managing network security policies manually (or with multiple, inconsistent tools), Aberdeen has developed a straightforward Monte Carlo model using the standard functionality of Microsoft Excel. Personalization of various contextual factors is also enabled, by supporting the selection of:
- The number of sites with firewall installations (across the entire enterprise)
- The number of firewall vendors (across all sites)
- The total number of firewalls
- The amount of annual revenue supported by the network
- The number of users supported by the network
The model makes use of Aberdeen’s estimates for the range (i.e., lower bound, upper bound) and shape for each of the following high-level factors of operational cost and security-related risk:
- The operational cost of managing network security policies is based on estimates for the number of changes to policies, rules, and configurations throughout the enterprise; the time it takes to review, check, approve, implement, test, and validate these adds or changes; and the fully-loaded cost of operational staff.
- The security-related risk of managing network security policies is based on estimates for the time the network is negatively affected by security-related issues (e.g., slowdown or downtime); the amount of annual revenue supported by the network, and the fraction of network-supported revenue lost during the period of slowdown or downtime; the number of users supported by the network, the fraction of user productivity lost during the period of slowdown or downtime, and the fully-loaded cost per user.
This analysis also establishes a baseline for quantifying the value of an incremental investment in a security policy management solution (this case is provided in the next section).
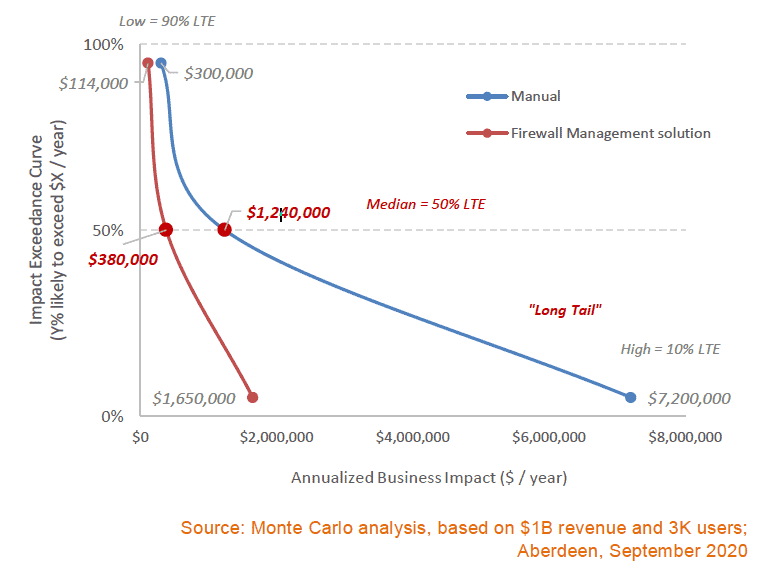
As a specific example, consider a larger network infrastructure (20 total firewalls, over four sites, from three different firewall vendors) in the private sector, which supports $1B in annual revenue and 3,000 users:
- The median total business impact of managing network security policies manually in this scenario is about $1.24M per year, with a range of $300K to a “long tail” of $7.2M.
- This range reflects an 80% confidence interval — i.e., 90% likely to exceed a relatively modest $300K, 10% likely to exceed a more significant $7.2M, and a median (50% likely) value of $1.24M.
- These three points are highly typical of the range and “ski-slope” shape of an exceedance curve in cybersecurity — where the important, risk-based business decisions are usually made at the worst-case side of the curve (i.e., from the median to the long tail).
Based on these estimates from their subject-matter experts and trusted advisors, some senior business leaders may choose to accept the risk of managing the network firewall infrastructure manually and stick with the status quo. Others may find this level of risk to be unacceptably high, and ask for recommendations on ways to manage it to an acceptable level. As always, the primary role of the IT and Security professional is to identify, assess, and communicate the likelihood and impact in a way that helps the owners of the risk to make a better-informed business decision.
Sidebar: For a larger network infrastructure (20 total firewalls, over 4 sites, from 3 different firewall vendors) in the private sector, which supports $1B in annual revenue and 3K users, the median total business impact of managing network security policies manually is about $1.24M per year, as compared to about $380K per year with a security policy management solution.
Quantifying the value of an investment in a network security policy management solution
A straightforward extension to Aberdeen’s Monte Carlo model provides invaluable insights into the most natural follow-on question from the business decision-maker: how would an investment in a security policy management solution quantifiably reduce operational costs and security-related risks? This requires estimating ranges and distributions for just two additional factors:
- The relative effectiveness of a security policy management solution, as a much faster and more accurate way to review, check, approve, implement, test, and validate adds or changes to firewall policies, rules, and configurations. In particular, a security policy management solution can automate the most routine tasks, such as submitting and reviewing policy request forms; technology and policy checks for new rule creation; submission and approval of change management ticketing; and implementation, testing, and change validation of new rules.
- The incremental annualized cost of implementing and operating a security policy management solution, which must be tallied as part of the business impact in the “after” scenario — i.e., we need to count not only the benefits, but also the costs.
Sidebar: The key to automation is visibility, particularly in complex and dynamic hybrid cloud environments.
In a “shared responsibility” model, the cloud service providers deliver the architecture, integration, optimization, security, and operational aspects for the lower levels of the application computing infrastructure stack.
Even so, the enterprise subscribers still must govern and manage the more strategic (e.g., policy) aspects of their entire infrastructure, including both on-premises and public cloud deployments. This requires active monitoring and policy-based decision-making.
Leading security policy management solution providers are now using API-based integration to provide the real-time visibility necessary to enable this level of centralized governance and management — and to achieve the quantifiable benefits of automation.
Based on estimates for these two factors shared with Aberdeen by a leading network security policy management solution provider, Aberdeen’s Monte Carlo model quantifies the value of security policy management in the same illustrative scenario:
- After the implementation of a security policy management solution, the median total business impact is about $380K per year, with a range of $114K to a “long tail” of $1.65M.
- Compared to a manual management approach, this represents a reduction in the total business impact of about 3.3 times at the median, and a reduction of about 4.4 times at the “long tail.”
- At the median, this an annual ROI of about 7.5 times.
A visualization of the total annualized business impact of managing network security policies in this scenario, comparing the “manual” and “policy management” cases, is shown as Figure 1.
Figure 1: Quantifying the Operational Cost and Security-Related Risk of Managing Network Security Policies, and the Value of a Security Policy Management Solution
Additional insights: Breaking down the business impact
An additional benefit of modeling the two high-level factors of operational cost and security-related risk for managing network security policies across an increasingly complex IT infrastructure is that it provides additional insights into which makes the greatest contribution to the total annualized business impact.
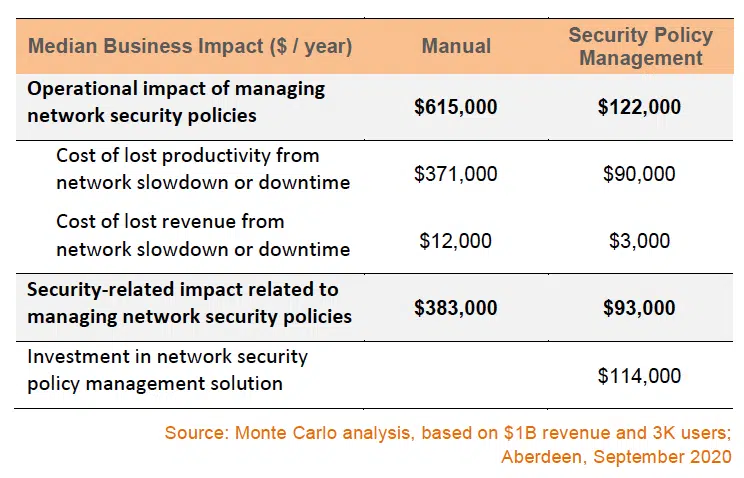
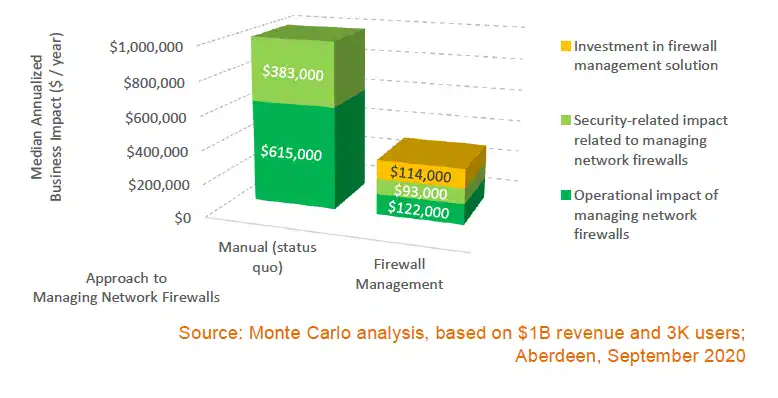
As seen in Table 1 and again in Figure 2, it turns out that the operational cost of managing adds and changes to firewall policies, rules, and configurations across a complex, hybrid network infrastructure is by far the biggest factor, followed by the lost productivity of users as a result of network slowdown or downtime. Think of these figures as a double-click drill-down on the red circles that represent the median (50% likelihood) level of total business impact as shown in Figure 1.
Table 1: Double-Click Drill-Down on the Median (50% Likely) Level of Total Business Impact
Figure 2: Total Annualized Business Impact of Managing Network Security Policies is Dominated by Operational Cost of Managing Adds and Changes, Followed by Cost of Lost User Productivity
From the perspective of making a business case for an investment in a security policy management solution, there are two solid arguments:
- The most tangible benefit of security policy management is to reduce the day-to-day burden on operational staff — by reducing time and improving accuracy for managing network security policies, rules, and configurations — through automation, integration, and real-time visibility throughout your network security infrastructure. This is in the “hard” category of cost savings.
- The strategic benefit of security policy management is to reduce the security-related risk of network slowdown and downtime on the productivity of the organization’s users — i.e., a strong enable the business message, and direct support for increased flexibility and agility of a hybrid on-premises / cloud-based IT infrastructure. This is in the “softer” category of cost avoidance.
In Aberdeen’s view, the operational efficiencies alone — in this scenario, a 4.3 times annual return on investment at the median, in terms of cost savings — justify the investment in a network security policy management solution.
In addition, security policy management contributes directly to avoiding the costs of security-related risks from network slowdown and downtime — in this scenario, an estimated 2.5 times return on investment at the median — by helping to keep the organization’s network infrastructure and network-dependent resources up, running, and productive.
In an environment where literally hundreds of cybersecurity solutions are competing to make the cut in terms of enterprise priorities and budgets, the one-two punch of benefitting both operational cost and security-related risk makes network security policy management worth a closer look.