Perspectives on Automation Imperatives, Inhibitors, Talent & Budget
Based on the current global macroeconomics construct, there is little sign that budgets will rise during H1 2021. That said, ever increasingly complex automated attackers are identifying new vulnerabilities and activating new enterprise breaches. Unfortunately and inevitably, some of those breaches are becoming true incidents. Automating Enterprise Cyber Security and Cyber AI have, for many seemed like a nice-to-have here-to-fore. That simply will not be the case moving forward.
Cyber security executives are now separating the wheat from the chaff in the Automation solution search. Finding a provider with demonstrable results is a must. CISOs are taking a collaborative proactive stance in responding to the current- and conceiving of the coming- threat landscape. As the industry collectively marches forth, we take the opportunity to release our Automating Enterprise Cyber Security Report.
Automation Imperatives
The universal imperative is of course reducing business risk by ensuring cyber security executives are spending time actually securing the enterprise. Automation offers the promises of increasing efficiencies and reducing costs across the enterprise. With an influx of threat intelligence technologies and feeds available to the organization, it is quite easy to get bogged down in non-actionable information. The key is to focus cyber security humans on only high-impact actionable information. Thus automation should be responsible for collecting data, correlating information, identify meaning and suggesting proper actions.
FOCUS
Our Cyber Security Hub Mid Year Report on Spend and Trends revealed that two in five executives list SIEM and SOAR automation technologies as solutions that have been the biggest priorities in the last 6 months:
28 SIEM + 11 SOAR = 39% (61% other)
Roughly three in ten in the Cyber Security Hub community have taken advantage of Security Information and Event Management (SIEM) to date. But current detractors of the technology note that SIEM systems only shed more and unnecessarily detailed information on the issue without solving the problem. That means that cyber security analysts now have to wade through volumes and volumes of white noise as opposed to focusing on actionable information.
SIEM VS. SOAR
Thus many see SIEM technology as a precursor to Security Orchestration, Automation and Response (SOAR) systems. The “And Response” part of SOAR suggests the automation of responses. That is the goal- gaining actual intelligence from information to orchestrate automatic remediation. Unfortunately the true effectiveness of SOAR technologies is still conceptual for a good portion of the industry.
While SIEM and SOAR technologies are in focus, there is a suggestion from the cyber security community that the technologies themselves could stand to be improved. DBS Bank’s VP Information Securty, Santosh Kamane shares, “Automation right now is meant to find out, where are there violations to my policies? And who is violating my standards? So there could be hundreds of logs created from the tools, but the tools are not very easy to read, or easy to understand as they are very technical.”
Sidebar
7 Security Policy Automation Questions
Does it improve people or process efficiency?
How can it be measured?
Does it result in greater consistency?
Can it be quantified?
How does it reduce risk?
Are research skills aligned to achieve the
defined objectives?
Does it save the company money?
Tim Woods, FireMon
PROMISE VS. ACTUALIZATION
Beyond the industry looking for improvements in the technology, executives would also like to see more accuracy in the messaging around solutions, “A lot of vendors at the moment have marketing around AI and machine learning and how that fits into the automation piece. I think some companies are doing good things in this space, but there’s still a way to go as far as automated responses to threats.” That’s Horizon Power CISO, Jeff Campbell who suggests that automation solutions- at this point- shouldn’t be considered plug and play.
There is an industry disconnect between solution promise and solution actualization. There is a perception that the current solution capability promise from providers does not contextualize the internal resourcing needed to actualize the intended results.
RESOURCING
There are executives at very large institutions that are confident in the results of SOAR technologies and capable of resourcing those solutions from an internal- already employed- analyst perspective. Thus those executives are very pleased with the solutions they have acquired. For others a key focus may necessarily be on a more direct Phishing Protection or Email Filtering solution based on the lack of elasticity in current staffing numbers and a shortage of the specific skills needed for automation technologies within the current staff.
Please see more information on resourcing below in the Automation Talent section.
Automation Inhibitors
There are innumerable inhibitors to cyber security automation. Processes are never perfect. A human though, can institute a workaround for a process and potentially catch vulnerabilities when those processes run at human speed. When automating a broken process, the results of that broken process are realized much more quickly. That means unfound and potentially exponential vulnerabilities can be exposed and not realized until a breach occurs.
The issue of automation itself is just one inhibitor. A lack of standardization around automation processes and solutions means global cyber security executives are not singing off of the same hymn sheet thus laying the groundwork for further vulnerabilities. While standardization is a goal, so is customization. The complexity of cyber security systems demands a fair amount of customization around automation technologies. Customization of technologies exposes weaknesses as well as lengthens the time and cost associated with implementation.
LACK OF STANDARDIZATION
The move to a primarily distributed workforce has destabilized any standardization that was in place in Q1 2020. While cyber security executives have undertaken a herculean feat to optimize remote environments, work still needs to be completed. Thus compatibility of legacy systems with newer off premise tools is not ideal. Without optimal compatibility and interoperability of systems standardization is challenging. Without standardization, rules-based automation is difficult.
DIFFICULTY WITH CUSTOMIZATION
“Finding a technology that understands your environment, understands what normal is, identifies that anomalous behavior, and then executes an automated response to that anomalous behavior is elusive.”
Jeff Campbell, CISO, Horizon Power
TIME
One of the key promises of Automation is to save cyber security teams time. With systems up and running and appropriately resourced- that in fact would be the case. But systems that work for your particular environment need to be found, proven to work within your environment, rolled-out, fully implemented, tweaked and resourced. From a standing start, that is a six-month process when things go smoothly and there are no other impediments to the project.
SKILL
The search for and rollout of an automation tool is simply the foundation of automated insights informing cogent security decisions within the enterprise. CISOs are realizing that no matter how much a technology partner points to the low code or no code nature of the technology, internal scripting and coding must occur to get the most out of automation systems.
“There are organizations right now that are using a threat hunting methodology to find and evict threat actors before they actually have a long-standing persistence. The trick there is to do it manually once, and then figure out how to automate. You can then focus on new types of threat hunting or new types of playbook, thereby making your staff way more effective without necessarily increasing your staff or necessarily increasing your risk.”
Kayne McGladrey, IEEE
COST
Even though the promise of saving money through efficiencies warrants action and potential spend- the actual spend is hard to outlay for many at this moment. There are more than a few cyber security operations who blew through this year’s budget and a bit of next year’s budget just getting above water in Q2, 2020.
5 Questions to help gain certainty from automation
What is the provider going to do to guarantee ROI?
What does the internal team need to do to guarantee ROI?
Can the provider cite real world evidence of achieve ROI?
What is the true investment on security dollars?
Where will return be seen (consistency, efficiency, improved posture, improved security)?
Tim Woods, FireMon
Automation Controls
With automation responsible for collecting data, correlating information, identify meaning and suggesting proper actions, the question becomes what other controls can be automated. When asked, the Cyber Security Hub community provided myriad opportunities where automation can accomplish the principle of increasing efficiencies and reducing costs within cyber security.
Apart from logs, there are many:
Identifying vulnerabilities
Running penetration testing
Engaging an ethical hacker, to run automated tools and manual scripts
Finding the remediation
Expediting the reporting
Finding patterns in the trending data
Engaging data analytics to build something meaningful out of your logs
And acquiring analysis of enterprise behavioral patterns
Santosh Kamane, DBS Bank
Remediation & Workflows
Remediation, with the caveat that it works well in the IT space but not so well in the OT space. Within OT, it’s all about availability. Apart from remediation, automation can assist workflows around incident management and automating some of those workflows. Automation can integrate into a ticketing system, which will then raise an alert with your SOC team to action. So identifying your use cases, building a workflow around the use case and automating the workflow.
Jeff Campbell, Horizon Power
It’s hard to find a technical control that cannot be automated at this point.
- The traditional things that are around identity and access management can be automated
- Data loss prevention (DLP) can be automated
- Threat hunting can be automated Ingestion of threat intelligence feeds can be automated (Assuming you think of them as just a data feed and you don’t actually think of them as an intelligence feed. Intelligence is a human intelligence function, not something you automate.)
- Endpoint Detection Response (EDR), can be automated by filtering out the false positives
Kayne McGladrey, IEEE
Security at the Speed of Change
The reality of today’s problem is that business is moving faster than our ability to secure it. The controls that we’re putting in place just aren’t honoring the speed of business. To get ahead of this, we need to think about how we will automate firewall operations and network security policy enforcement.
Tim Woods, FireMon
Automation Talent
The goal of automation is to reduce the burden on the people who have less time and less time to execute more and more tasks. But in-house talent is not necessarily easily shifted to help with automation. Automation is most valuable when the in-house team is responsible for coding ensuring seamless integration and interoperability of all of your systems. The abundance of talent needed in DevSecOps foreshadows and overlaps with the abundance of talent needed in automation.
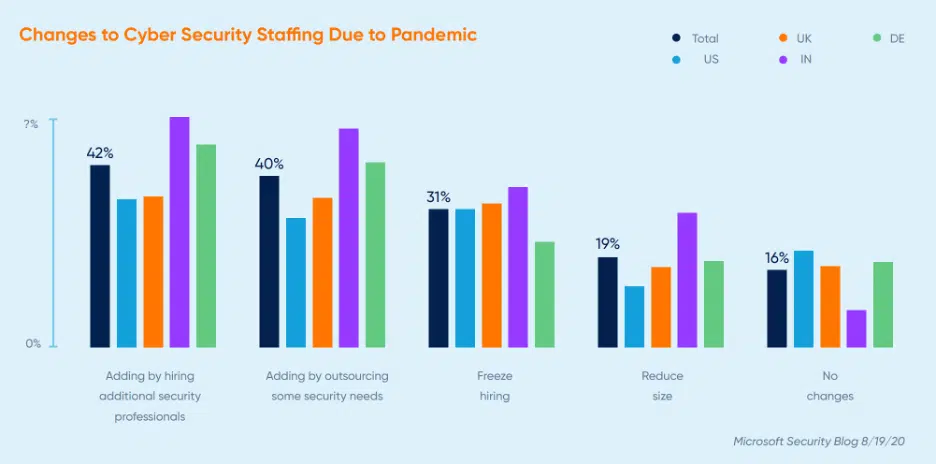
The coming Cyber Security Hub Year End Report features the fact CISOs want to add staff in 2021 but that budgets are likely to remain static or to be reduced. Leaders have also noted that some of the 2021 budget has already been spent in 2020 due to immediate distributed workforce related needs. The Microsoft Security blog paints a similar picture in that budget had increased in the wake of the pandemic and that a good section plans to add staff moving forward. But even with bullish executives responses, two in three expect either no change, to freeze or to reduce staff.
Different Skillsets
“Automation, particularly in the AI and ML space, requires a good understanding of mathematics and algorithms that support mathematical response to anomalies. So finding good mathematics people that understand the computer science domain will always be a challenge I think, because there are very few individuals that actually have a real, really deep passion for mathematics.”
Jeff Campbell, Horizon Power

Platform vs. Defense-In-Depth
“While it the might not do the latest, greatest bestest thing, the advantage of going with a platformbased solution, is that it sure does 90% of what you need and typically all of the tooling is integrated. That reduces implementation time because it’s got a common design language in the user interface, it’s got a common way of working, which really does reduce the amount of learning time associated for people. Every time we bring in a new tool into the organization, you have to have somebody who learns it. And that takes time away from their daily duties. You can’t just learn a tool while you’re fighting a fire. That’s not how the world works.”
Kayne McGladrey, IEEE
Finite Time & Talent Can Be Expanded With A Touch Of Automation
Whether you look at a number that says 69% of organizations have understaffed security teams or 350,000 unfilled positions in the industry, it’s clear that the resources that we have are getting stretched too thin. As an industry, we’re making compromises in our security profile. And when we make compromises, bad things happen.
Tim Woods, FireMon