The increasing complexity of networks, driven by the constant influx of cloud services, new devices, and applications, presents a daunting challenge for managing firewall policies and rules. A typical enterprise environment has millions of rules, and just one simple misconfiguration can lead to devastating consequences like compliance violations, outages, and data breaches.
FIREMON
Security Manager
Consolidated policy and rule management for firewalls and cloud network security groups
Complexity is Unavoidable. Headaches Don’t Have to Be.
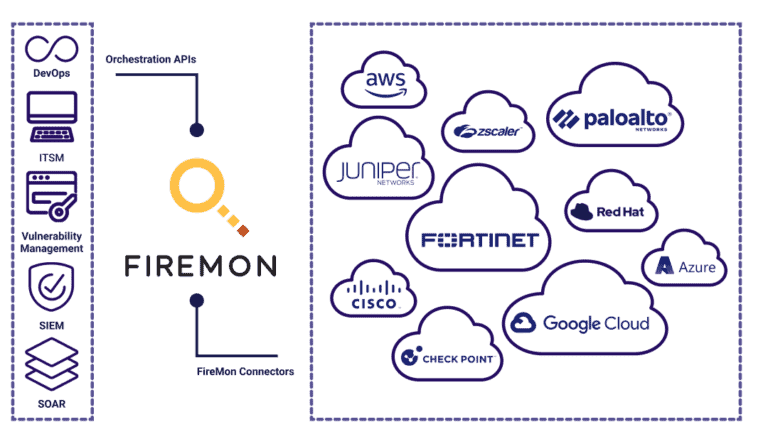
FireMon Security Manager
FireMon’s Security Manager is a purpose-built network security policy management (NSPM) platform that automates the management of firewall and cloud security policies to eliminate policy-related risk, accurately and quickly change rules, and meet internal and external compliance requirements.
- Reduce Risk Manage risk with real-time visibility and control
- Manage Change Avoid misconfigurations, accelerate business, and improve security
- Enforce and Maintain Compliance Avoid violations, avoid risk, and avoid fines

Security Manager Features
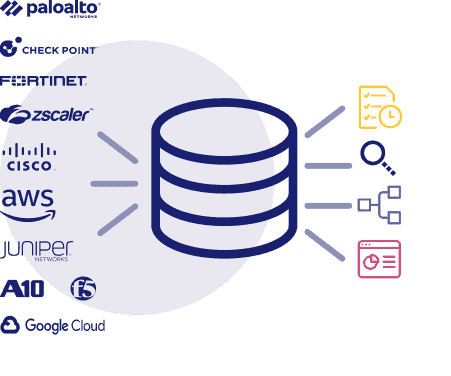
Real-Time Inventory of Devices and Rules
FireMon’s Security Manager platform creates a centralized rule repository that automatically imports information that translates into a common, normalized rulebase, providing a comprehensive view of an organization’s security posture.
- Real-time single source of policy information
- Automatically identifies and imports information into a consolidated rule repository
- Support for over 80 vendors and versions for network policy normalization
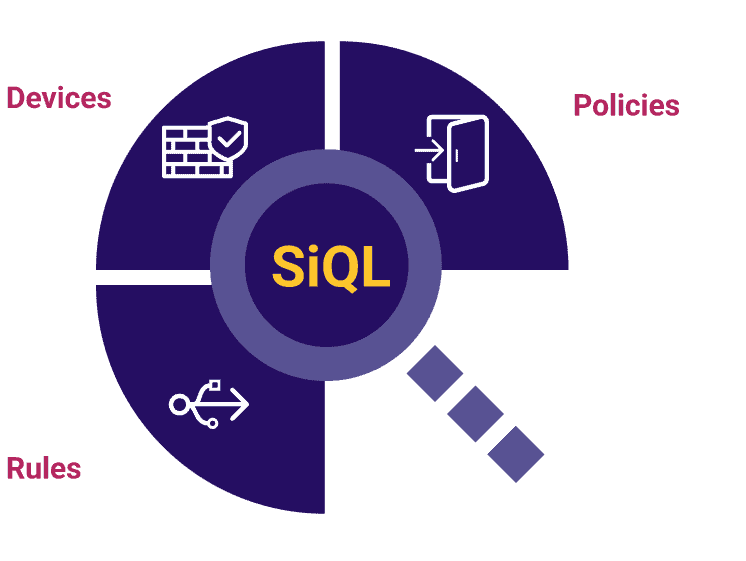
Search Across the Entire Environment
FireMon’s proprietary Security Intelligence Query Language (SiQL) enables fast and customizable search of network policies across various elements in the platform, including workflows and users, allowing users to search policies across their entire environment from a single environment.
- Less than 10 seconds to return real-time results
- Fully customizable
- Powers customizable controls and rule review criteria

Consolidated Compliance and Risk Assessments
FireMon’s unmatched reporting capabilities offer over 20 preconfigured compliance and assessment reports that can be customized, as well as access path analysis and “what if” attack assessments, with the option to integrate vulnerability scanner and risk/threat modeling for enhanced security.
- Over 500 preconfigured criteria checks
- Unified dashboard for an overall view of risk and compliance using FireMon’s Security Concern Index
- Vulnerability integrations including Qualys, Rapid7, and Tenable give deeper insights to policy-related risks
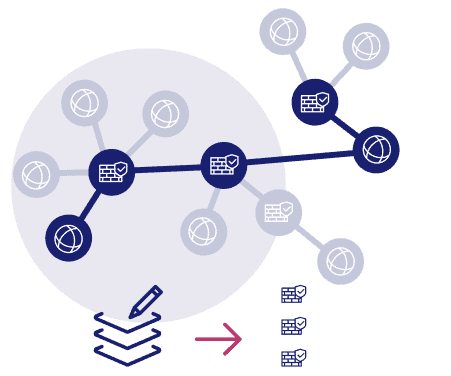
Simplify Rule Creation and Updates
FireMon’s rule management tools simplify rule creation and updates by providing detailed recommendations on device changes needed to deploy new or update existing rules, with integration with leading ITSM systems allowing for automatic or manual changes during approved change windows, while evaluating them for risk and compliance violations before deployment.
- Workflows with intelligent rule recommendations
- Automatic rule evaluation tests for violations and risk before it’s deployed
- Make changes yourself or use FireMon’s optional automatic rule deployment

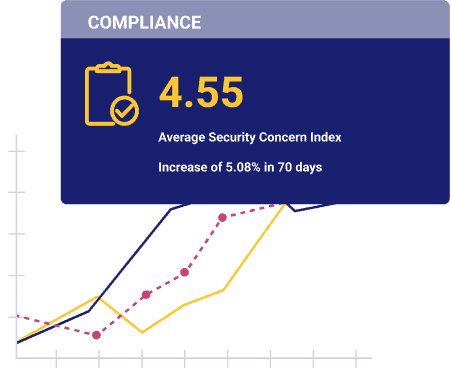
Rule Review and Recertification
FireMon’s policy lifecycle management feature offers automated workflows for regular rule assessments, sends rule review emails to policy owners triggered by SiQL searches or periodic reviews, and allows recertification or decertification of the rule with flexible workflows that track all information needed for compliance audits.
- Event-based triggers and customizable workflows assign and notify owners of relevant policy violations and rule reviews
- Centralized audit tracking records all actions taken on a rule providing accurate compliance reporting
- Customizable rule treatment options allow for rule certification, decertification, or decommissioning, with option to automate decommissioning with our Policy Planner module
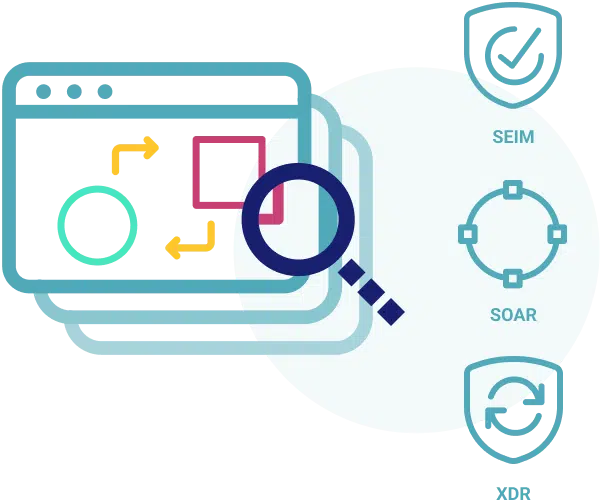
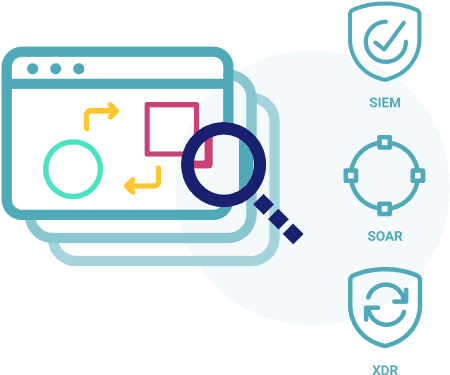
API-First for Maximum Integration Flexibility
Our API-based integrations with various security vendors like IBM, Rapid 7, AWS and Azure, along with our API-first approach that exposes all platform elements and functionality via Swagger-based APIs, significantly reduce the need for professional services to set up our platform in your environment.
- Native and API-based integration with security vendors in the SIEM, SOAR, vulnerability detection, cloud, DevOps, ITSM, SASE, SD-WAN, networking, and endpoint categories
- API-first approach exposes platform element and functionality via Swagger-based APIs
Architecture Built for Scale
FireMon’s Security Manager is designed for complex enterprise environments achieved through a distributed architecture that separates the application, database, and data collectors on separate servers for seamless scalability.
- Purpose-built to address the needs of the most complex and demanding enterprise environments
- Every release certified to support 15,000 devices and 25 million rules
- Sub-10 second response times for search and report generation
Security Manager Features At-A-Glace
| Security Manager Base |
Change Management Add-on |
Rule Recertification Add-on |
Vulnerability Management Add-on |
|
|---|---|---|---|---|
| Centralized rule repository | ||||
| Multi-vendor rule normalization | ||||
| Rule usage summary | ||||
| Security Concern Index to measure risk over time | ||||
| Control failure summary | ||||
| Vulnerability assessment | ||||
| Change history and documentation | ||||
| SiQL Search | ||||
| Preconfigured assessments | ||||
| Customizable reporting | ||||
| Preconfigured controls | ||||
| Customizable controls | ||||
| Access Path Analysis | ||||
| What-if attack scenario simulations | ||||
| Vulnerability scanner integration, including Qualys and Rapid7 | ||||
| Customizable rule creation/change workflows | ||||
| Intelligent rule design recommendations | ||||
| Pre-deployment compliance/risk assessments | ||||
| Automatic rule deployment to devices | ||||
| Customizable rule review workflows | ||||
| Event-driven review triggers | ||||
| ITSM integration; including ServiceNow | ||||
| SIEM integration | ||||
| SOAR integration | ||||
| Swagger-based API integration |

